What is it and how can I configure an API Identity?
What is an API Identity?
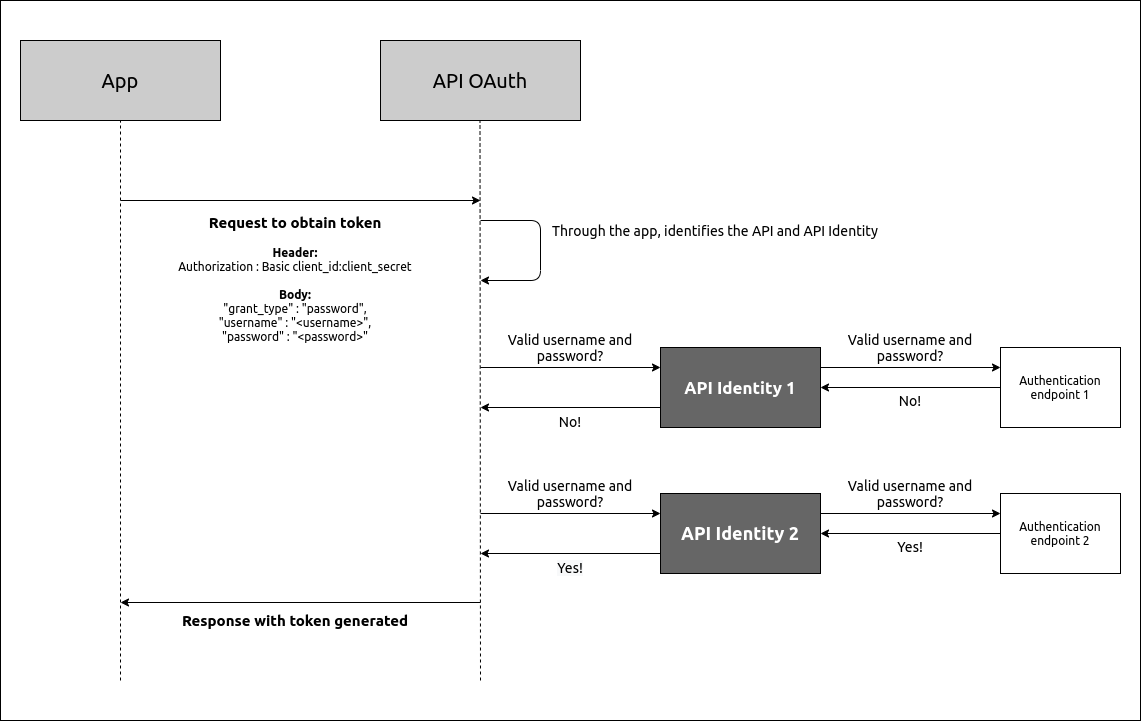
API Identity is a type of API that we created just to facilitate authentication via the OAuth Password flow.
First, let’s understand what the Password flow is:
Now, the central question:
Every API that requires the Password flow to generate and validate access tokens must be linked to an API Identity (this link is made in the registration of the API Identity).
This API and the API Identity must be deployed to the same environment.
Other than that, for the API Identity to be able to handle calls for token generation, it must be deployed in the same environment as the POST / access-token flow (that is, in the same environment as the API OAuth, which comes with your Manager).
How to configure an API Identity?
The configuration of an API Identity follows the same steps as for a normal API. The difference is that there is an extra step in the case of Identity, in which we need to link it to the API that will require access tokens generated with the Password.
See more
-
We detail the calls required to obtain access tokens through the Password flow here.
-
If you want to read more about the differences between the OAuth flows, access The OAuth 2.0 Authorization Framework.
Share your suggestions with us!
Click here and then [+ Submit idea]