XSS Threat Protection
This interceptor protects calls against malicious scripts that may be injected into the elements (body, headers, URL segments or query params) present in the requests and responses generated by the operations of your API.
The interceptor can be configured with a set of regular expressions, capable of identifying patterns of scripts that perform XSS (cross-site scripting) attacks, thus preventing the call from being completed if a malicious script is found.
Configuring the interceptor
When using the XSS Threat Protection interceptor for the first time, users can see that it is pre-configured with a set of standard regular expressions, and they are placed in the four key locations where a script injection may occur: URI_PATH, QUERY_PARAM, HEADER and BODY.
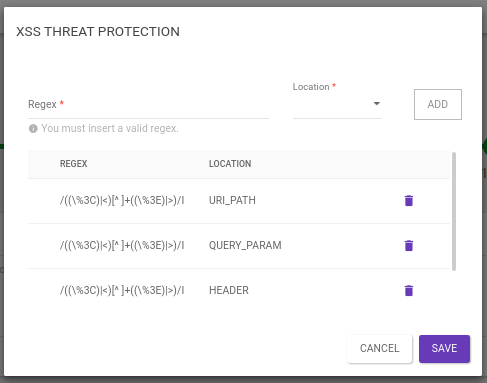
The interceptor may be saved with this default settings or, if necessary, other expressions can be inserted.
The interceptor can be placed both in the request and response flows.
How it works
During its execution, the interceptor will check and execute all regular expressions saved. If any malicious script pattern is found, the interceptor will block the the flow from continuing — be it the request or response flow — and two log lines will be added to the General Trace, indicating which expression was executed.
Share your suggestions with us!
Click here and then [+ Submit idea]