JSON Threat Protection
JSON Threat Protection is an interceptor that validates the contents of a JSON based on length, depth and number of elements for several components. This can avoid malicious attacks with illegitimate values.
To set up the interceptor, we have to fill in some properties, as shown in the image below. Then, each field is described.
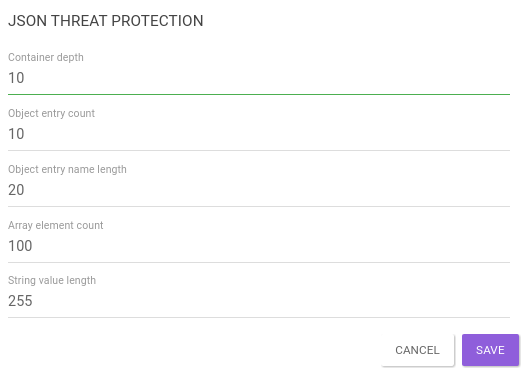
Fields
Container depth
It specifies the depth of an object.
Example of a JSON with depth 3:
{
"name": "Sensedia",
"city": {
"name": "Campinas",
"uf": {
"name": "SP"
}
}
}Object entry count
It specifies the number of attributes in an object.
Example of a JSON with 4 attributes:
{
"city": {
"name": "Campinas",
"uf": "SP",
"foundation": 1774,
"population": 1204073
}
}Object Entry name length
It specifies the number of characters of an attribute.
In this example, the quantity is 4 characters:
{"city":"Campinas"}Array element count
It specifies the number of elements within an array.
Example of an array with 6 elements:
{
"years": [
2000,
2001,
2002,
2003,
2004,
2005
]
}String value length
It specifies the number of characters of the value of any attribute.
In this example, the quantity is 8 characters:
{"city":"Campinas"}Skip response if fail

It specifies whether to skip the response in case of failure. When this option is checked, if there is any error in the previous validations, the Gateway will not forward the request to the backend, but immediately return it to the client. This option is required when the JSON Threat Protection interceptor is configured both in the request and and in the response flow, thus avoiding validation conflicts.
Things to keep in mind
-
If all the properties of the interceptor are filled, the first validation that the Gateway sees will have its exception triggered.
-
If you want a property not to be validated, just leave its field blank.
-
If you select the interceptor, at least one of the properties must be filled.
-
By default, for POST and PUT requests, the HTTP header
Content-type: application/jsonmust be informed. Otherwise, an "HTTP 415: Unsupported Media Type" error is returned.
Flow
The interceptor can be inserted in both the request and response flows, as shown in the image below:
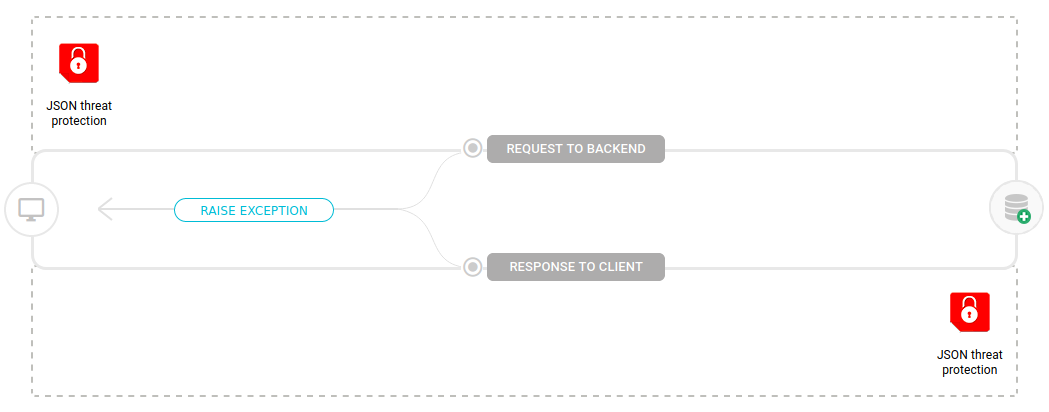
Errors
You can see below the errors that can be returned if the interceptor finds any anomaly.
| Title | Error | HTTP Code Request | HTTP Code Response |
|---|---|---|---|
JSON |
Json format invalid |
400 |
500 |
Container depth |
Container depth limit exceeds the maximum allowed for this API (10) |
400 |
500 |
Object entry count |
Object entry count limit exceeds the maximum allowed for this API (10) |
400 |
500 |
Object Entry name length |
Object entry name length limit exceeds the maximum allowed for this API (10) |
400 |
500 |
Array element count |
Array element count limit exceeds the maximum allowed for this API (30) |
400 |
500 |
String value length |
String value length limit exceeds the maximum allowed for this API (30) |
400 |
500 |
Invalid Content-Type |
JSON threat protection validation failed: Invalid Content-Type in Header → (Content type) |
415 |
415 |
Content-Type not found |
JSON threat protection validation failed: Content-Type not found in Header |
415 |
415 |
Share your suggestions with us!
Click here and then [+ Submit idea]