IP Filtering
With this interceptor, you can define a list of IP addresses whose requests will be blocked by the gateway or a list of the only IPs that will be allowed to make incoming requests.
|
The gateway works at the application layer, the validation is based on the header, and it is possible to manipulate the header values in the request. Therefore, ensure that only authorized persons have access. |
How it works
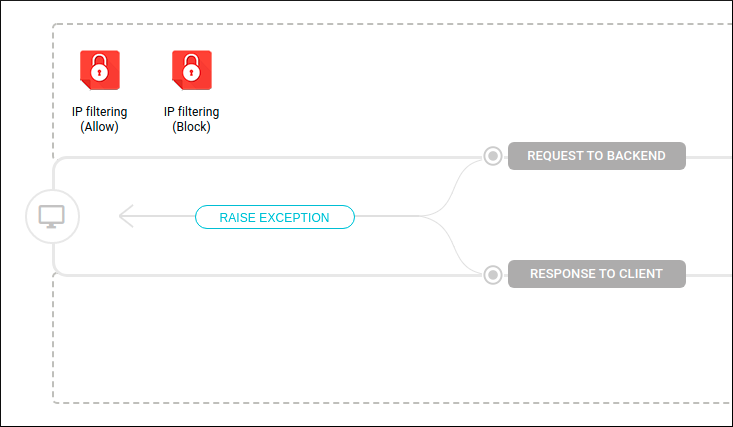
As IP Filtering is used to block or allow requests from specific IP addresses, it can only be added to an API’s request flow.
When configuring the interceptor, the user chooses whether it will be used to bar all requests coming from the specified IPs or whether it should only allow requests coming from these IPs and deny the requests from any other IP. It’s possible to include more than one IP at a time, either by entering each one individually or by including an IP range.
It’s also possible to make a combination of interceptors for allowing and blocking requests at the same time. As an example, imagine the configuration described below.
How to configure it
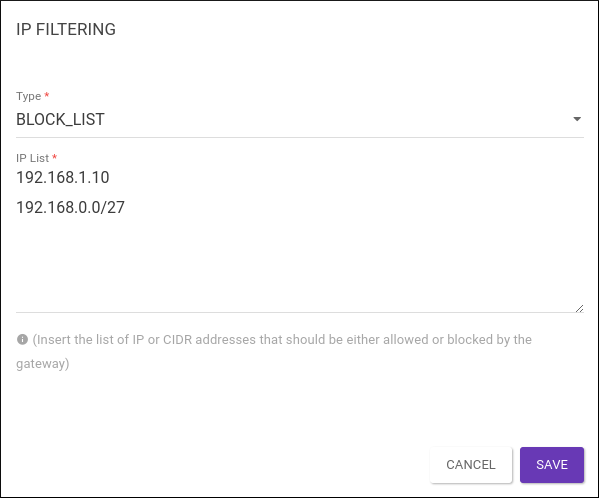
To configure it, you must choose the type of control. If it’s a BLOCK_LIST, you need to insert the IPs whose requests will be blocked in the IP List field. If you choose the type ALLOW_LIST instead, you must insert the IPs whose requests will be permitted. In the latter case, any IP which is not on the list will be blocked by the gateway.
You may include:
-
an individual IP (e.g.,
192.168.1.10); -
a range of IPs (e.g.
192.168.0.0/27); -
a list of individual IPs, IP ranges, or a mixed list — inserting one element per line, with no other separator. Example:
192.168.1.10 192.168.0.0/27
| When an IP range is configured, the broadcast and network IPs will always be ignored from validation, regardless of the configured range. |
The image below shows an example of a BLOCK_LIST in which an individual IP and an IP range will be prevented from sending requests.
Share your suggestions with us!
Click here and then [+ Submit idea]