Integrations
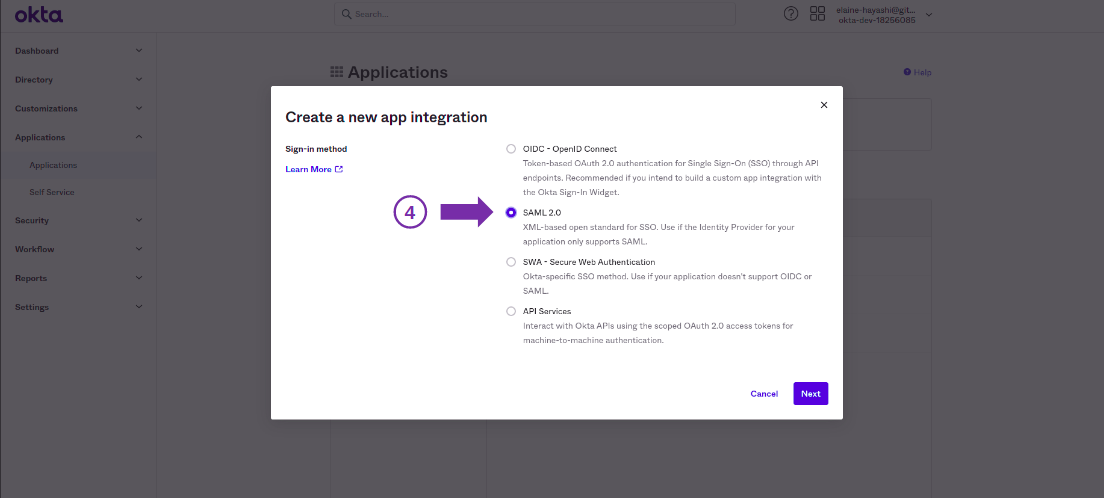
You can establish a connection via SAML with an identity provider so that users are able to log in to the API Manager using their credentials from that provider. The chosen provider must support the SAML 2.0 standard.
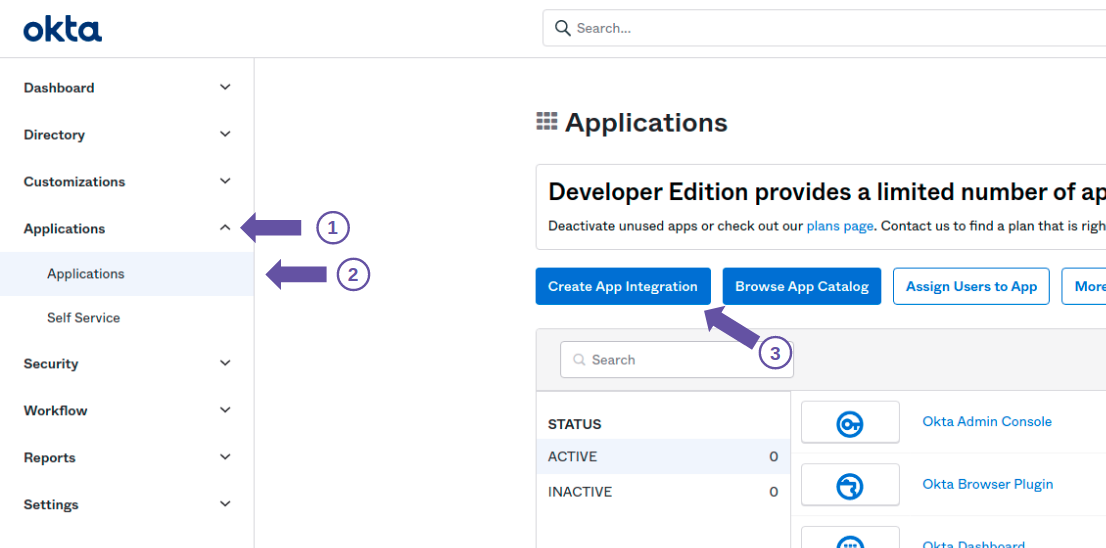
You can set up the connection on the Integrations screen.
| See below some useful tips to configure the integration with the API Manager on your provider. |
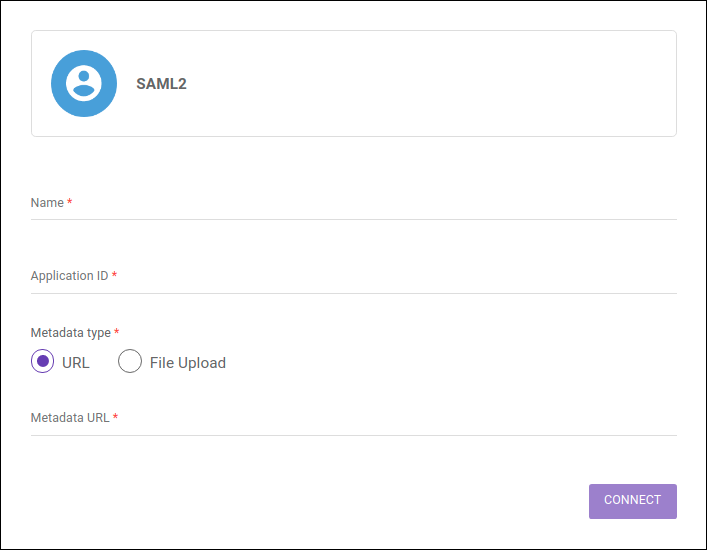
Configuring connection with SAML2.0
To set up a connection with an identity provider, complete these fields:
-
Name: include the name of your SAML provider.
-
Application ID: include the unique identifier of the API Manager within your SAML provider. It’s usually referred to as Application ID or Service Provider Entity ID. Check your provider’s documentation for more information.
-
Metadata Type: select if the metadata will be accessed via "URL" or "File Upload". To locate the Metadata URL or download a valid SAML file, check your identity provider’s documentation.
-
If "URL" is selected, type in the address in the field Metadata URL.
-
If "File Upload" is selected, click on METADATA UPLOAD and choose a metadata document from your machine.

-
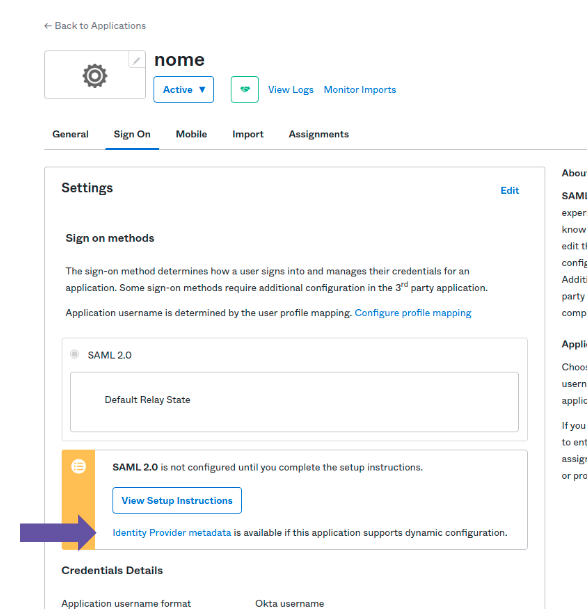
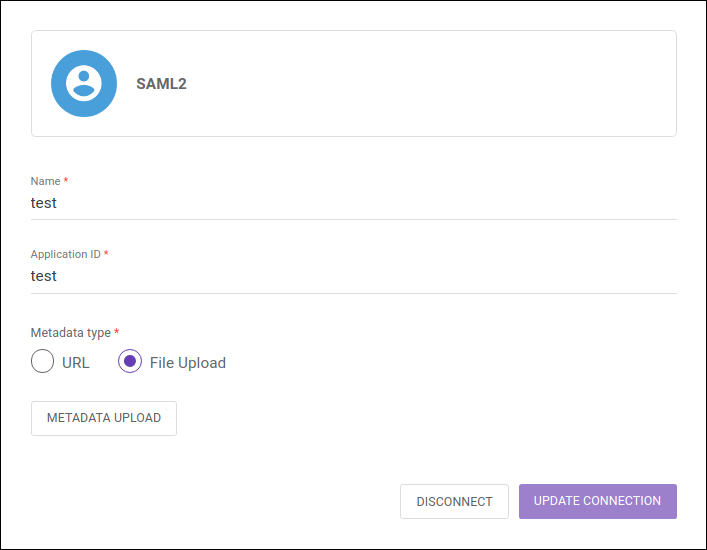
Deactivating or editing a connection with SAML 2.0.
Once active, the connection with the identity provider can be updated at any time. To do so, click any field you wish to edit, make the appropriate modifications and click on UPDATE CONNECTION.
To disable an active connection, click the button DISCONNECT. Users from the identity provider (regardless of whether they have been registered before or after the integration has been activated) will not be deleted from the Manager, but will have their access blocked until a password is created/reset — which can be done through the link Forgot your password? on the login screen.
User login and registration
Once a connection with an identity provider has been activated, the Manager login screen will change:

Upon clicking the button SIGN IN, the users will be taken to the login screen of the chosen identity provider and must enter their credentials for access. Users who had been registered on the Manager before the connection was active will no longer be able to log in using the username and password registered on the Manager, only their credentials from the identity provider.
In case it’s the user’s first access, they will automatically be included as a federated user in the Users screen and assigned the role "API Operations". The role can be changed later by editing the user on the Users screen.
| "API Operations" is a role that comes with your Manager. If it has been or is deleted, it will be recreated automatically whenever a new federated user is added. |
If a user that had already been created on the Manager (by the usual user registration process) logs in through the identity provider, their status on the Users screen will be changed to "Federated" but the role they already had will be kept (i.e., a Manager Admin user will be turned into a federated user but will keep the Admin role with all the role-specific permissions). See more about federated users here.
Tips for setting up an API Manager application on your identity provider
To enable a SAML 2.0 connection, an API Manager application must be registered in your identity provider. Your provider’s official documentation should help you with the necessary configurations, but some specific tips are helpful to ease the process:
-
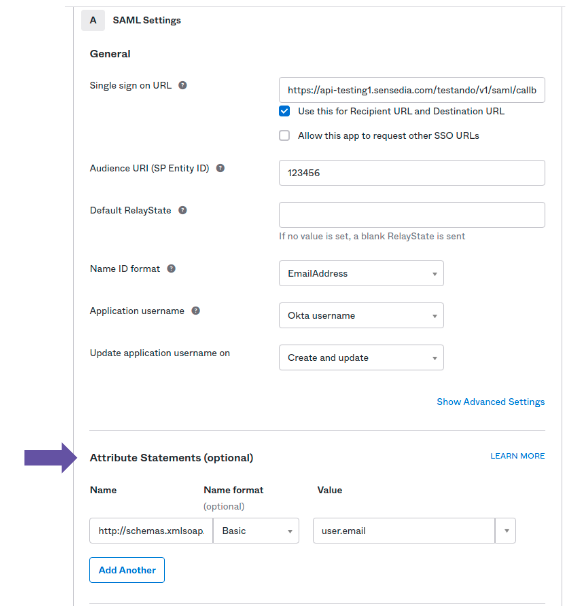
Configure the callback URL
You must include the callback URL (Single Sign On URL), which is based on your API Manager’s URL:<MANAGER-URL>/api-manager/api/v3/saml/callback. -
Set the email attribute
The provider must send to the Manager the users' email info as a SAML attribute. The name of the attribute must behttp://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddressand its type must beBasic. There may be small variations in the settings of each provider, so you might want to check their official documentation.
Share your suggestions with us!
Click here and then [+ Submit idea]