Concepts
Control plane
Set of modules related to design time. Functionalities such as environment configuration, APIs, policies and log visualization are provided by these modules. The control plane is shared.
| Although there are several mechanisms for high availability and resilience, it is not recommended to use administrative APIs in high load flows. |
Shard
The shard is a logical grouping used to provide services to a specific set of customers. Services such as database for logs and auditing tokens are shared with the data planes of a certain shard.
Data plane
Set of modules related to runtime. The data plane modules are dedicated to each customer. All calls are handled by modules contained in the data plane. Each data plane is provisioned in a dedicated VPC, with its own IP address. The data plane is composed of:
-
GW POOLS.
-
NETWORK LOAD BALANCER: Layer 4 load balancer.
-
SEC-PROXY: Responsible for TLS exposure and termination.
-
API GATEWAY: Responsible for transactions. Policy enforcement, logging, and transformations are performed by this module.
-
By default, the data plane is provisioned with a gateway pool (default), however, new gateway pools can be purchased.
In addition to gateway pools, other modules are available on the data plane:
-
API AUTHORIZATION: Module responsible for generating access-tokens.
-
MEMORY GRID: In-memory database for caching and data distribution.
In addition to these, there are some adjacent modules, also on the data plane.
Connectivity
The data plane can be connected to private environments to:
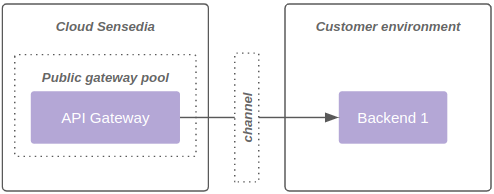
1 - Backend consumption for the public gateway pool, as shown in diagram 1:
2 - Consumption of the private gateway pool, as shown in diagram 2:
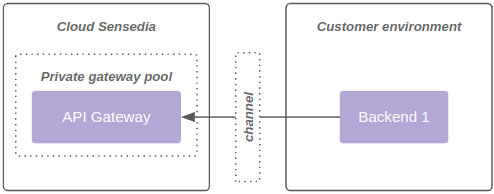
| A gateway pool cannot be public and private at the same time. |
Supported connectivity models
-
Allow list (Default)
-
Positive aspects
-
Most recommended model due to practicality and resilience.
-
Each data plane has at least 2 fixed output IPs. These IPs can/should be used for customer-side firewall controls.
-
To further enhance security, an mTLS strategy can be used between the gateways and the backend.
-
Cost already included in standard offers.
-
-
Limitations
-
It is not possible to access backends without externalization through a proxy or similar technology.
-
-
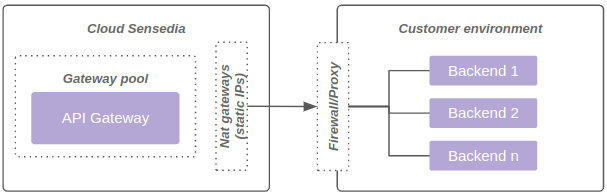
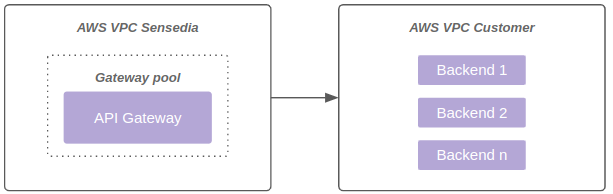
The diagram below represents connectivity through Allow list:
-
VPN (on request)
-
Positive aspects
-
Model with private access.
-
-
Attention points
-
Shared responsibility.
-
The SLA is different for VPN environments, given the high incidence of problems.
-
Higher cost of configuration, maintenance and troubleshooting.
-
-
Limitations
-
Each data plane can be connected to up to 4 networks, limited to 8190 IPs.
-
Currently, BGP is not supported.
-
-
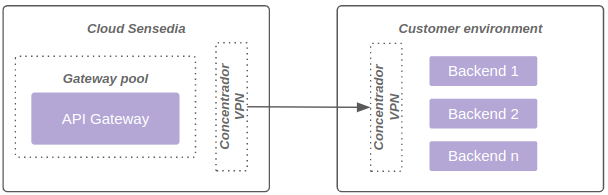
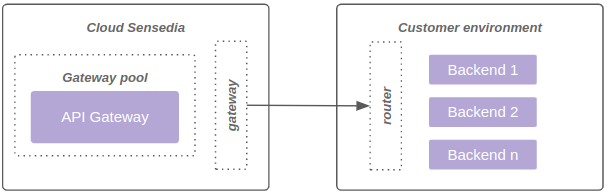
The diagram below represents connectivity through VPN:
-
VPC Peering (on request)
-
Positive aspects
-
Stability and resilience.
-
Simplified setup.
-
-
Attention points
-
Offer available only to customers whose backend is also allocated on AWS.
-
-
Limitations
-
Each data plane can be connected to up to 4 networks, limited to 8190 IPs.
-
-
The diagram below represents connectivity through VPC:
-
Direct Connect (on request)
-
Positive aspects
-
Possibility to access backends through a private link.
-
-
Attention points
-
Cost.
-
Shared responsibility model between Sensedia, customer and link provider.
-
-
Limitations
-
Each data plane can be connected to up to 4 networks, limited to 8190 IPs.
-
-
The diagram below represents connectivity through Direct Connect:
| Networks above 8190 hosts (/19) are not supported. |
-
Private link (on request)
-
Positive aspects
-
Facilitates communication between components on AWS.
-
Ensures private access with high resiliency.
-
For more information, see official AWS documentation.
-
-
Negative aspects
-
Requires exposure through NLB on the customer side.
-
-
Limitations
-
Up to 4 VPC endpoints (powered by AWS Private link) are supported per dataplane.
-
-
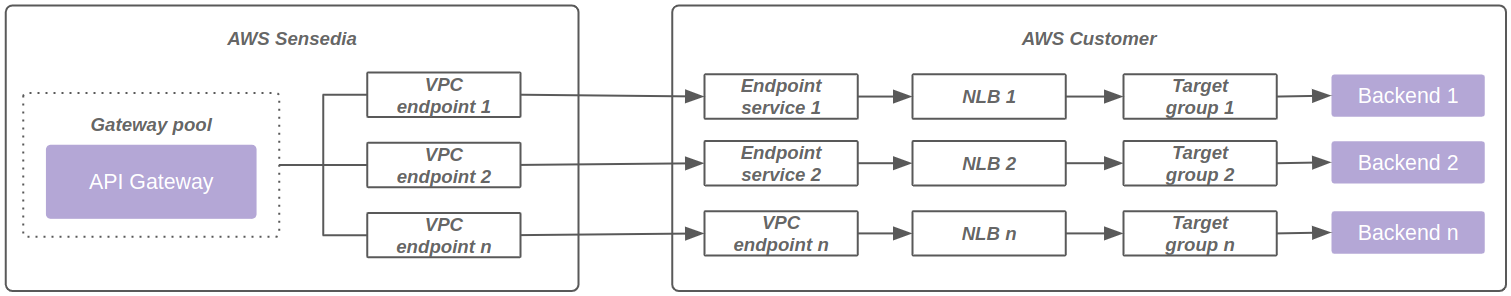
The diagram below represents connectivity using VPC endpoint powered by AWS Private link:
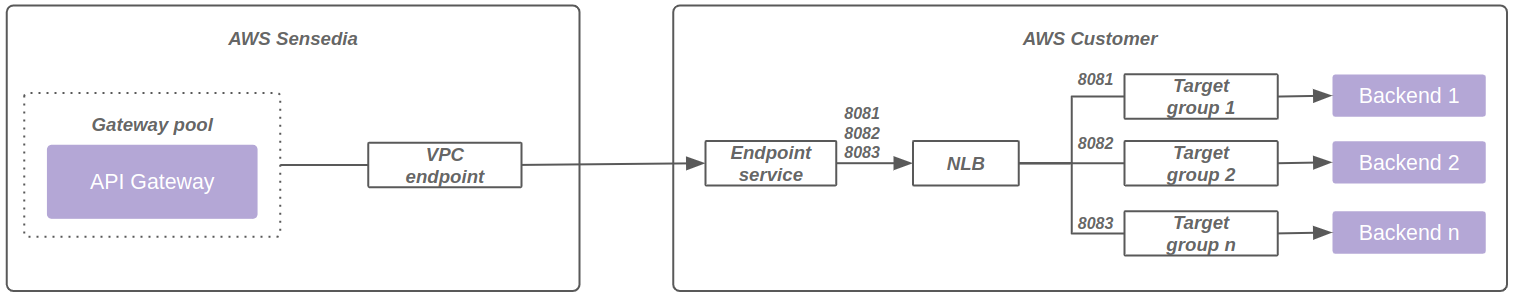
Additionally, it is possible to use the same VPC endpoint associated with the same load balancer, with multiple ports and target groups. The diagram below represents this model:
Share your suggestions with us!
Click here and then [+ Submit idea]