Authorization
The AUTHORIZATION tab allows creating, applying and visualizing authorization policy rules for a given service.
That is, this is where you can establish how access permissions are verified when requests are made to a service inside a given namespace.
Access permissions
The actions you can perform on this screen depend on the permissions set for your user in Sensedia Access Control.
The following table shows the possible permissions and the corresponding actions:
| Permission | Description |
|---|---|
List Api Authorizations |
It allows the view of the list with the authorization policy rules that have been created. |
Read Api Authorizations |
It allows the view of the details of the settings of the authorization policy rules that have already been created. |
Write Api Authorizations |
It allows the user to create, edit, and delete authorization policy rules for the services. |
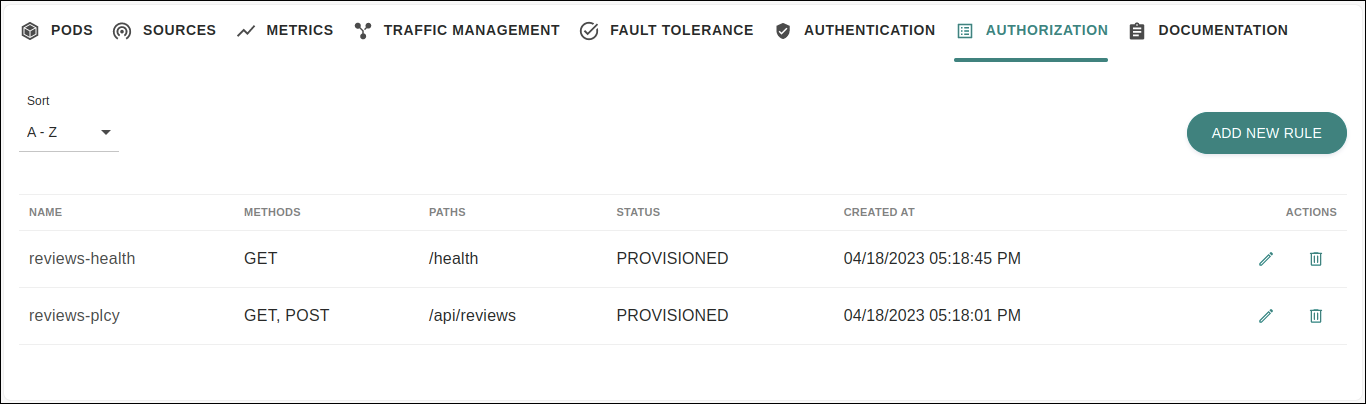
List of rules
The tab lists the authorization policy rules that are applied to a service, with the following information:
-
identifying name for the rule;
-
methods that are inside the scope of the rule;
-
endpoints the rule applies to;
-
service status;
-
date when the rule was created.
Also, the list contains action icons:
-
 to edit the rule; and
to edit the rule; and -
 to delete it.
to delete it.
Configuring authorization
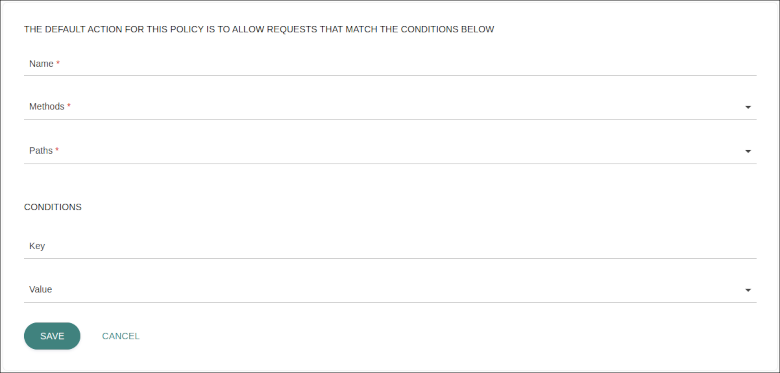
To set up a new authorization policy rule, click the button ADD NEW RULE and fill in these fields:
-
Name: identifying name for the rule, which must be unique to the namespace.
-
Methods: HTTP methods that are included in the scope being configured.
-
Paths: endpoint the rule applies to. More than one can be inserted.
-
CONDITIONS: non-required section to include optional attributes comprised of key and value. It’s possible to add more than one value per key. See the conditions you can use here.
Actions
Inside an Istio authorization policy rule, there is a field action which is responsible for telling Istio which policy will be applied to requests.
See an example of an Authorization object:
apiVersion: security.istio.io/v1beta1
kind: AuthorizationPolicy
metadata:
name: httpbin
namespace: foo
spec:
action: ALLOW
rules:
- from:
- source:
principals: ["cluster.local/ns/default/sa/sleep"]
- source:
namespaces: ["test"]
to:
- operation:
methods: ["GET"]
paths: ["/info*"]
- operation:
methods: ["POST"]
paths: ["/data"]
when:
- key: request.auth.claims[iss]
values: ["https://accounts.google.com"]On Sensedia Service Mesh, authorization policies are always created with action: ALLOW;
therefore, requests will be accepted only if they conform to the rules described under the key rules (and rejected if they don’t).
You can consult this documentation for more information regarding Authorization objects.
| If the Mesh Security option is enabled (on ), services will be blocked by default. Then, you’ll need to create authorization policies for all services you wish to allow access to. |
Share your suggestions with us!
Click here and then [+ Submit idea]