SAML 2.0
You can establish a connection via SAML with an identity provider so that users are able to log in to Sensedia products using their credentials from that provider. The chosen provider must support the SAML 2.0 standard.
|
Client Credentials cannot be generated using federated logins. |
|
When a federated login provider is deleted, all users associated with it are permanently deleted automatically and without prior notice. It is not possible to recover this data after deletion. |
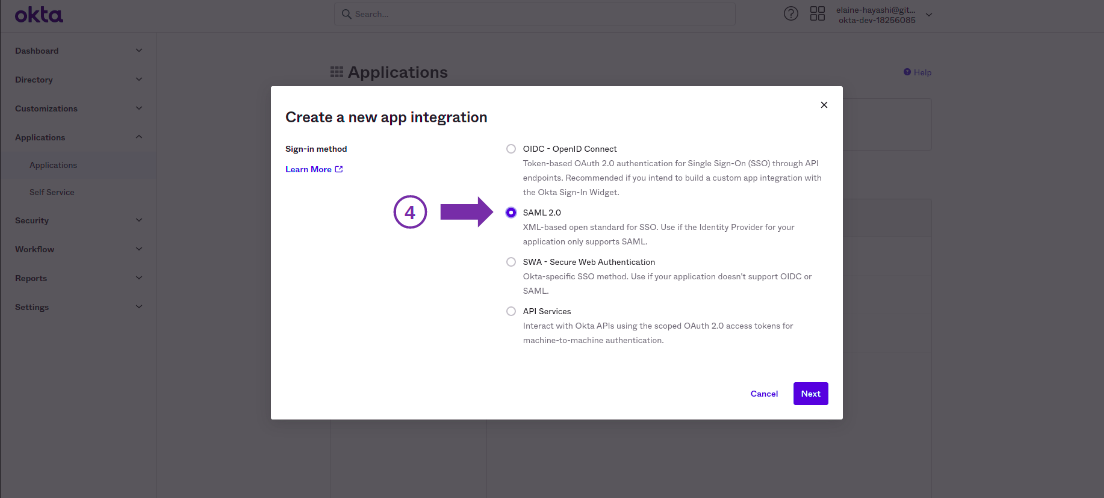
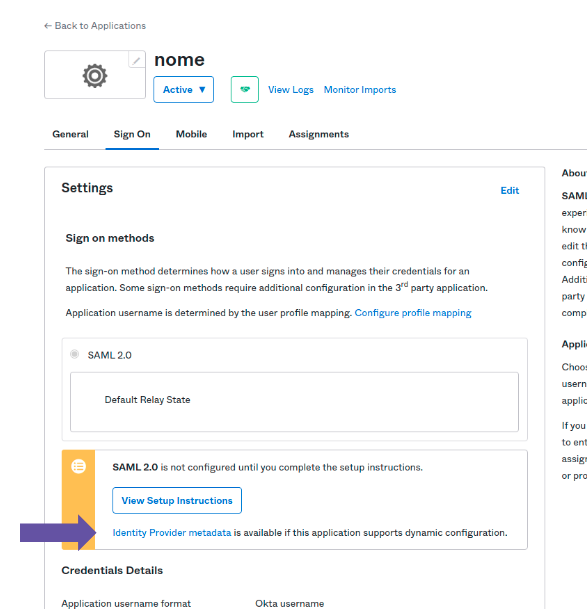
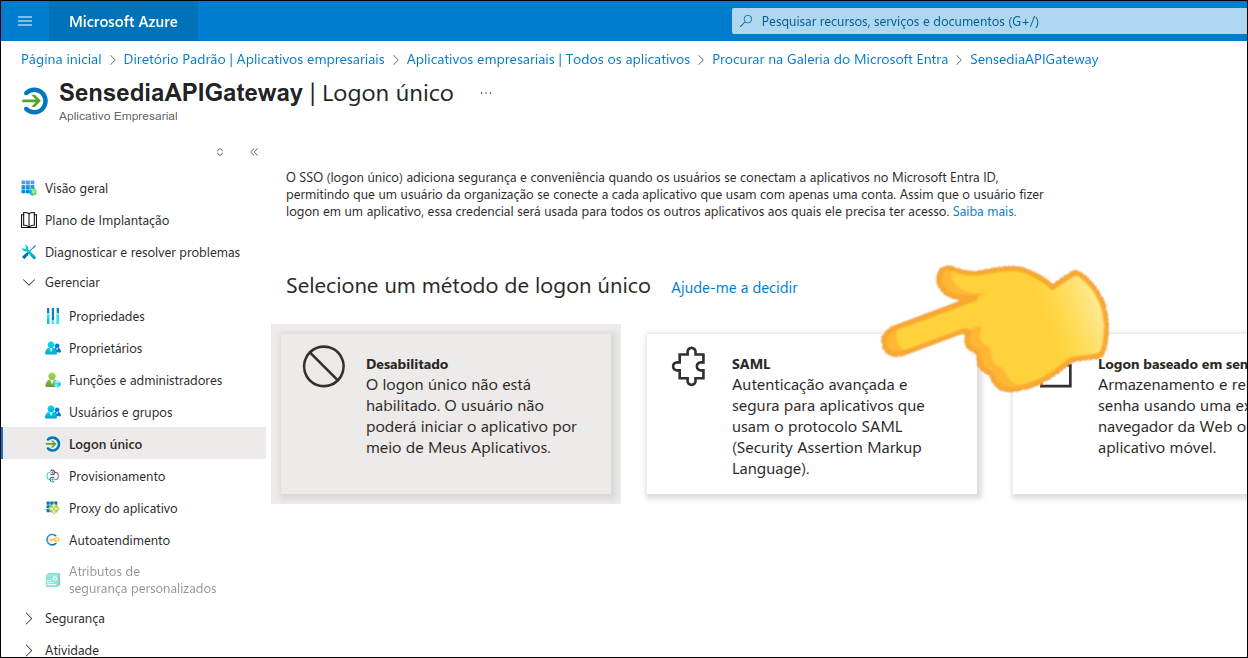
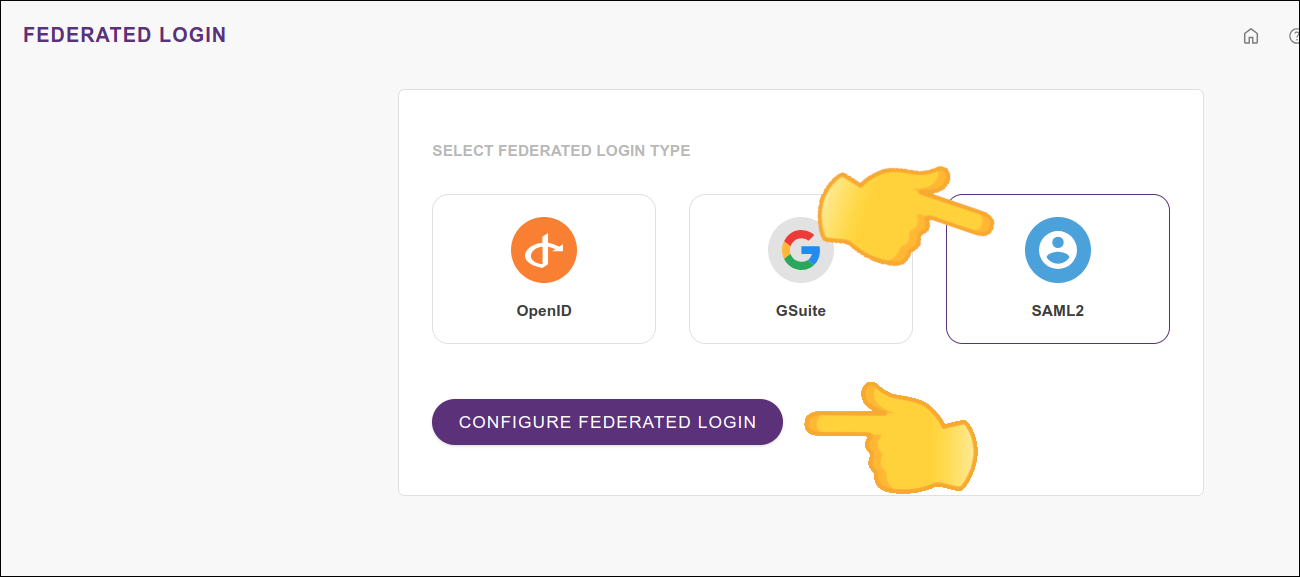
Configuring a connection with SAML2.0
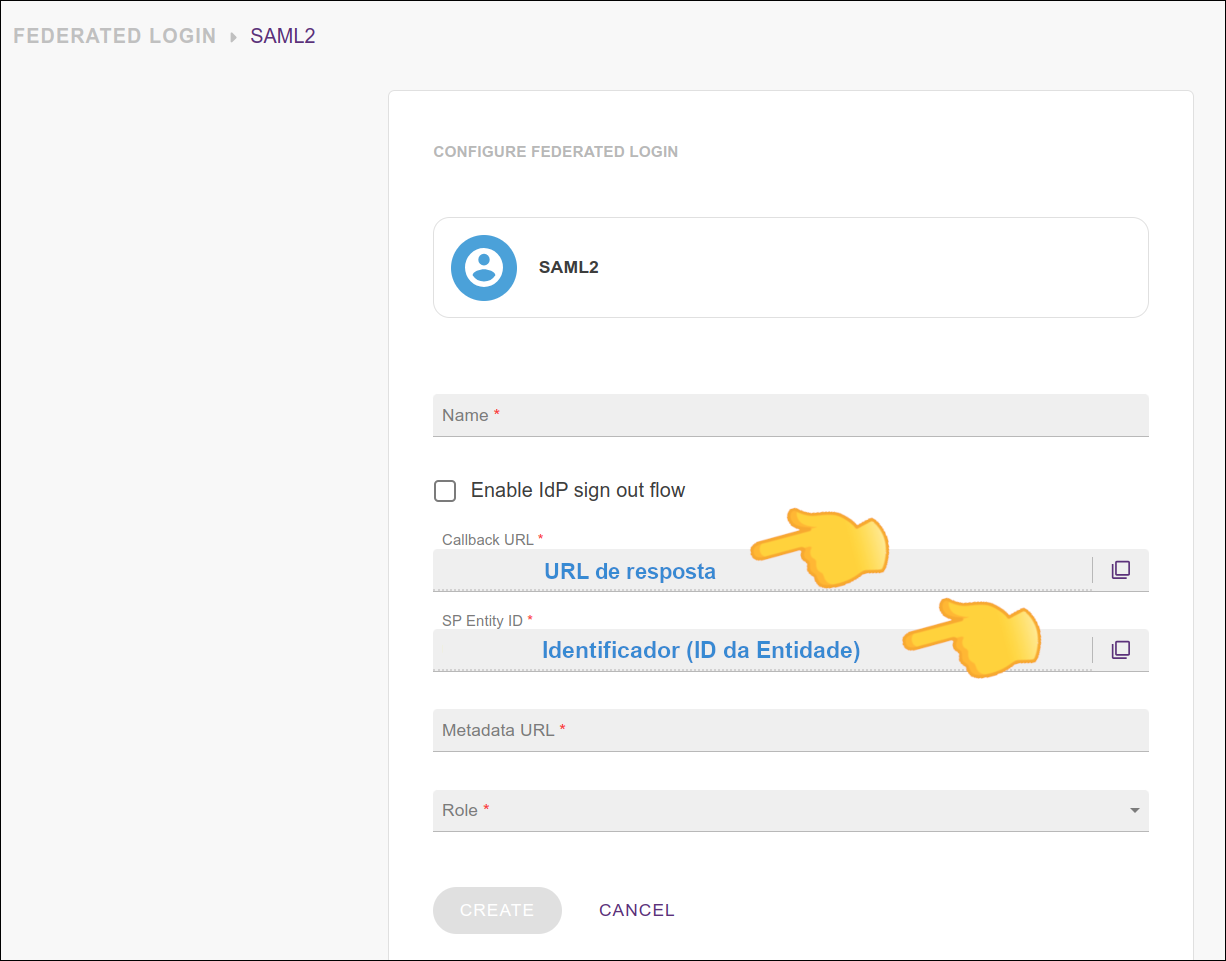
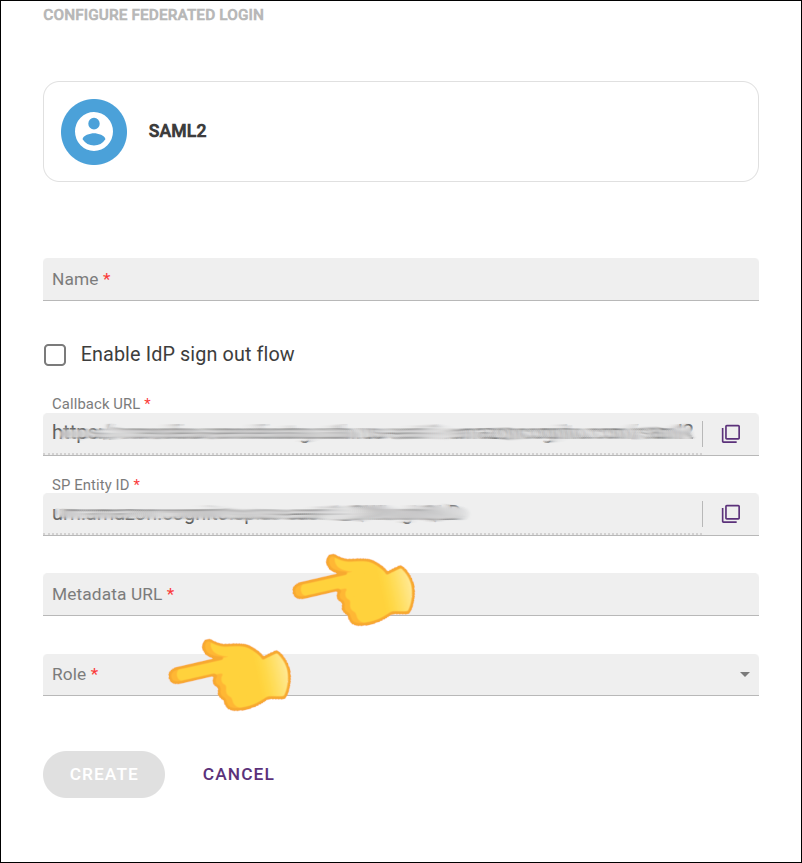
The configuration of a connection to an identity provider has the following items:
-
Name: name of your SAML provider.
-
Enable IdP sign out flow: For single logout (having your user logout of your IdP as well), select this option and use the information presented in the two fields that will be displayed to configure your IdP:
-
Logout URL and
-
Signing certificate.
-
-
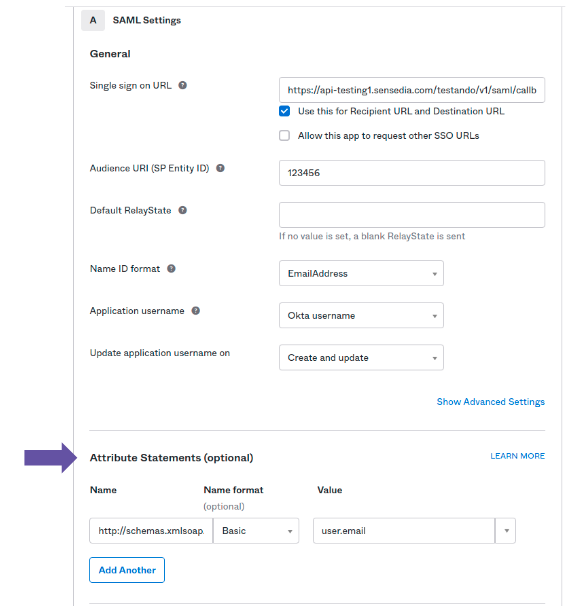
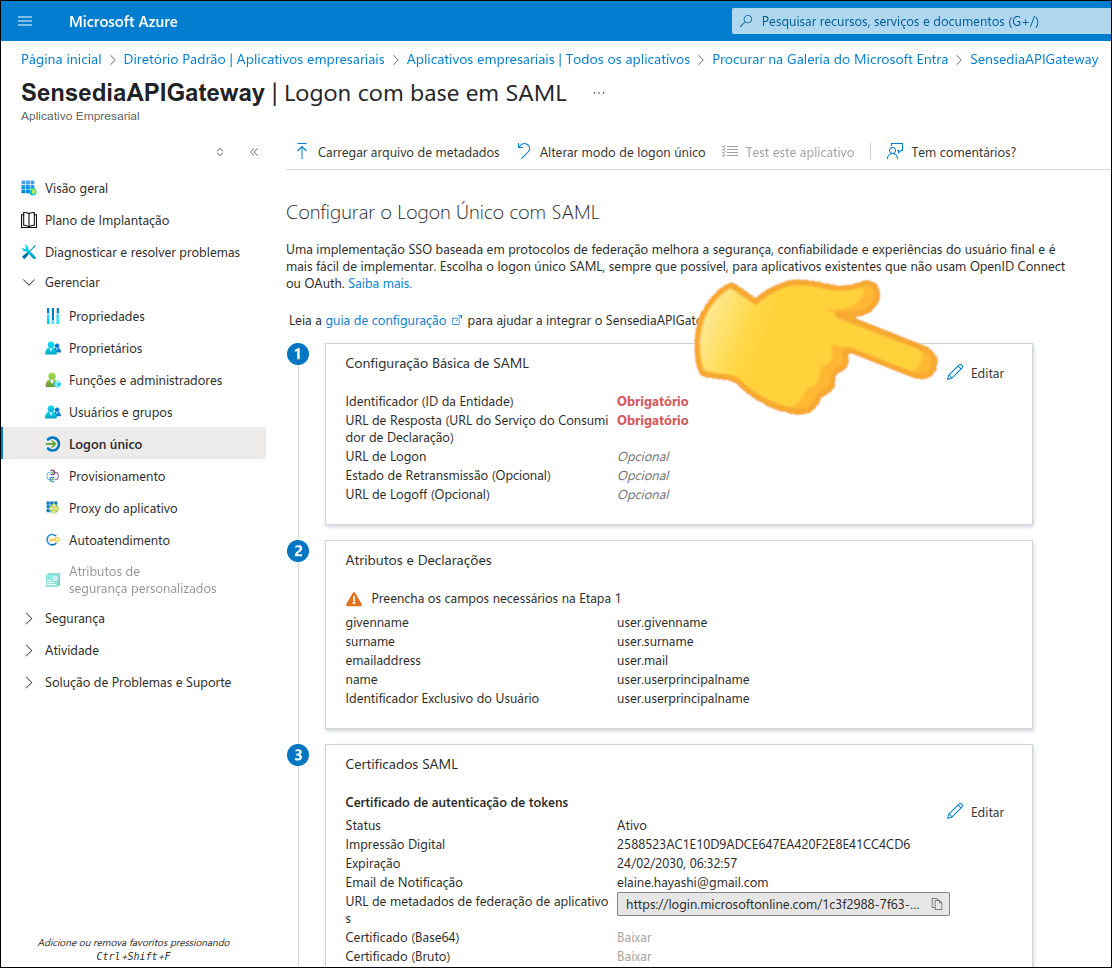
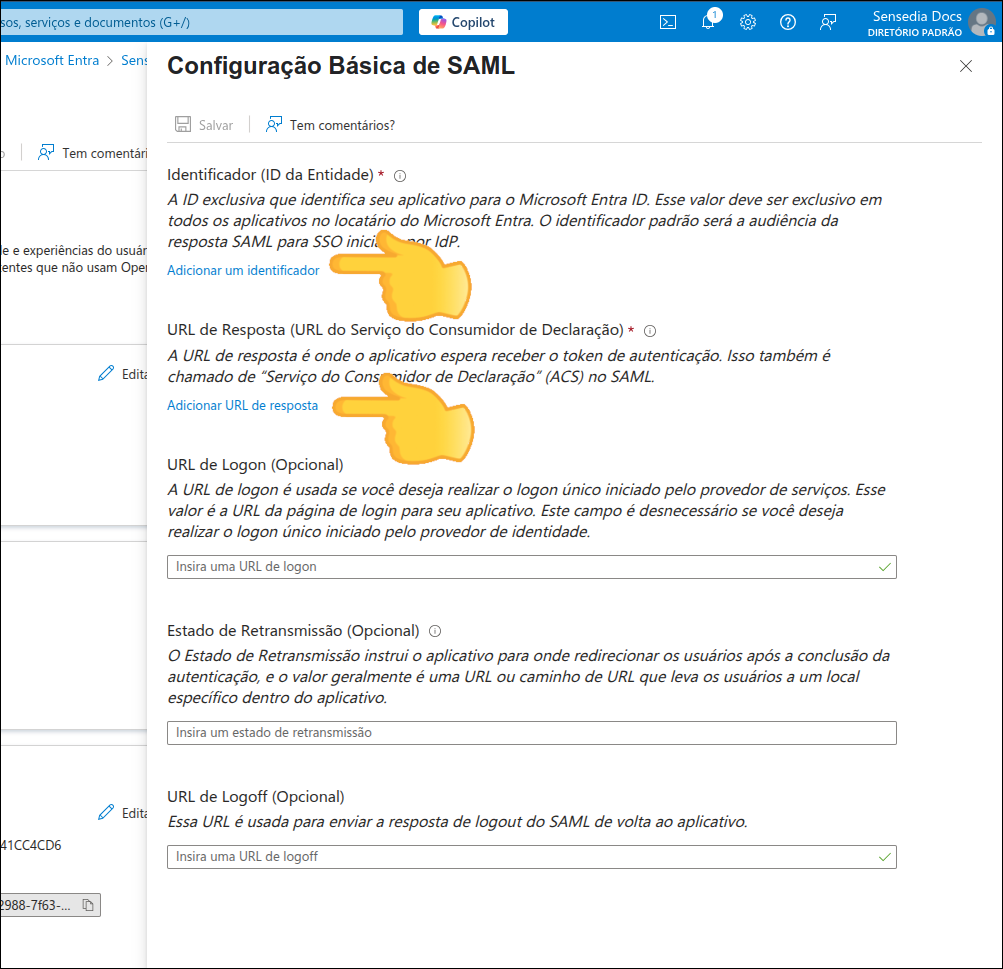
Callback URL: the URL to which your identity provider must return the user after authentication.
-
SP Entity ID: it is with this ID that your provider will identify your entity. Use this URN in the settings of your identity provider.
-
Metadata URL: the address to access the metadata. Check your identity provider’s documentation to get the Metadata URL and inform it in this field.
-
Role: select the role to be applied to this access.
| In case you have roles configured on your identity provider, they will override this one. |
Those fields are explained in the video below:
Deactivating or editing a connection with SAML 2.0
Once active, the connection to the identity provider can be updated at any time. To do so, click on any field you wish to edit, make the appropriate changes and click UPDATE.
To disable an active connection, click the DISCONNECT button.
|
The DISCONNECT button will disable the access of all users from that federated login. To reconnect, follow the steps above (Configuring a connection with SAML2.0). The DISCONNECT button does not change your settings in your Identity Provider. |
Login and control users
Unlike the log in process with Sensedia Platform, now the login with username and password is still possible even after configuring SAML 2.0.
A user will be able to log into Sensedia products either via SAML or separately.
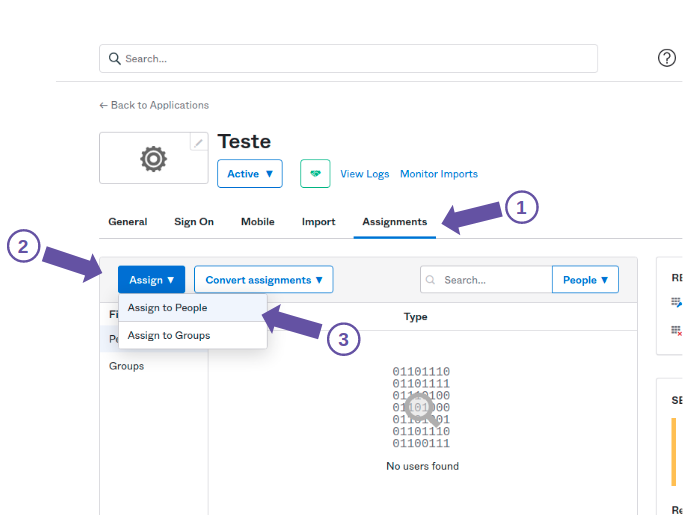
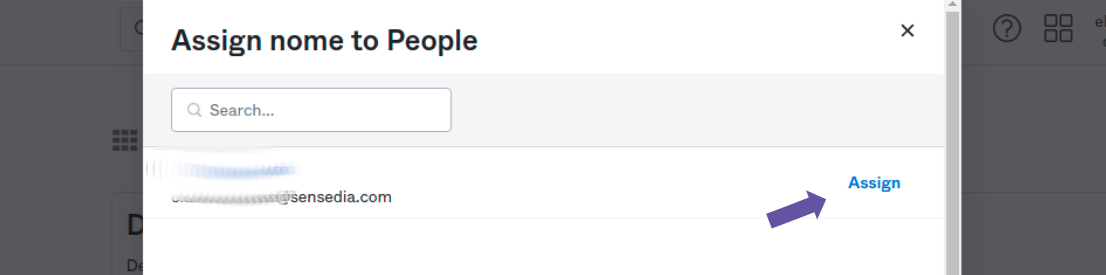
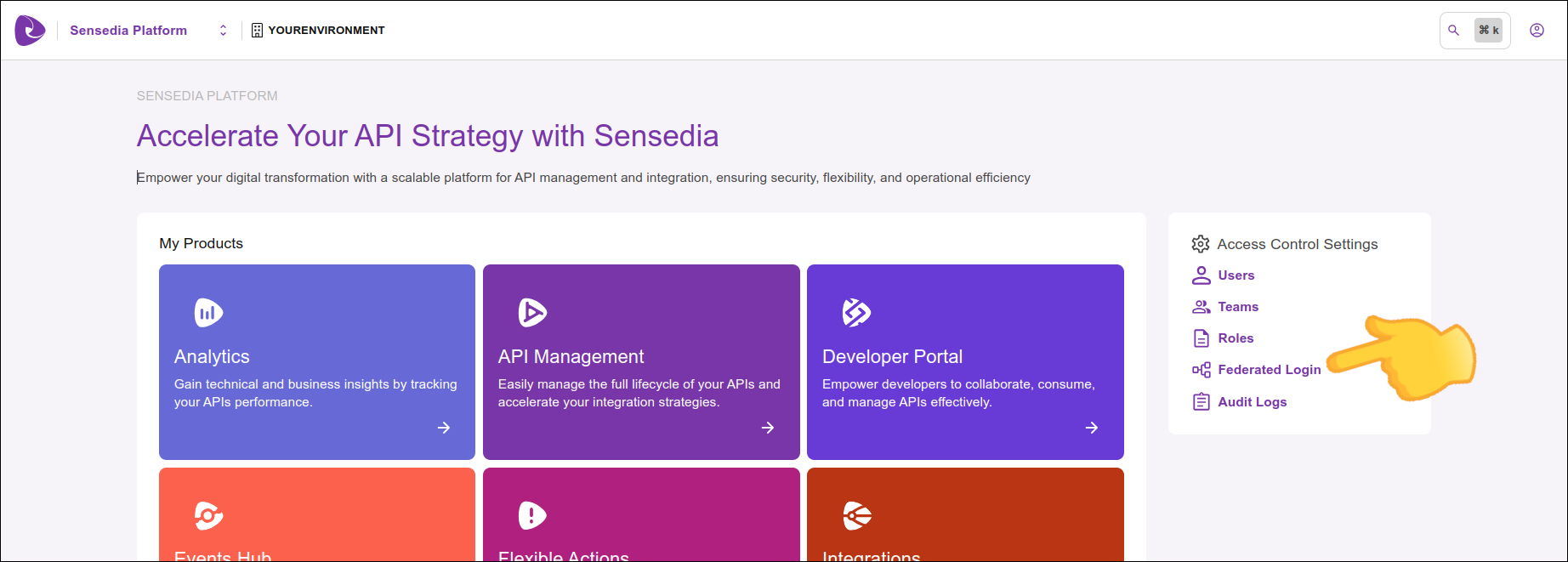
Setting up an API Manager application on your identity provider
To enable a SAML 2.0 connection, an API Manager application must be registered in your identity provider.
See below examples of configuration using:
| Please check your provider’s official documentation to find help with the necessary settings. |
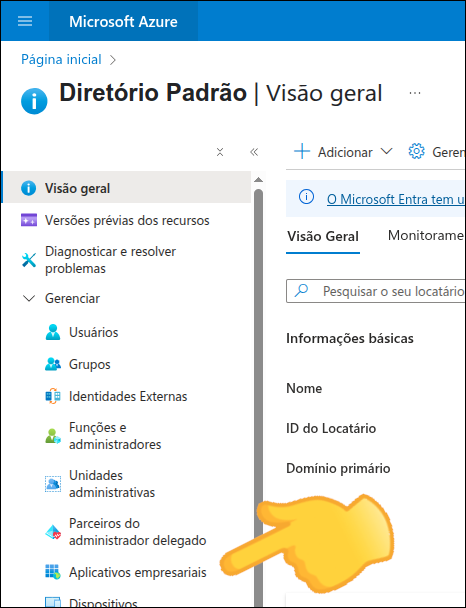
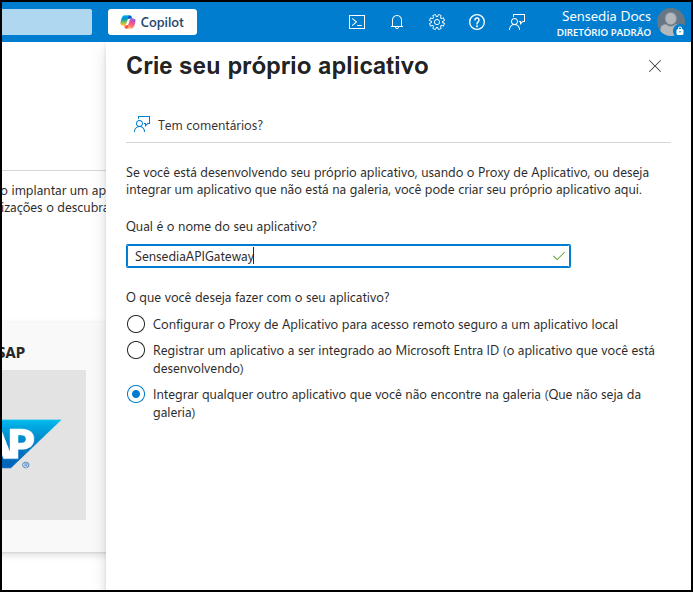
Example of configuration using Azure AD
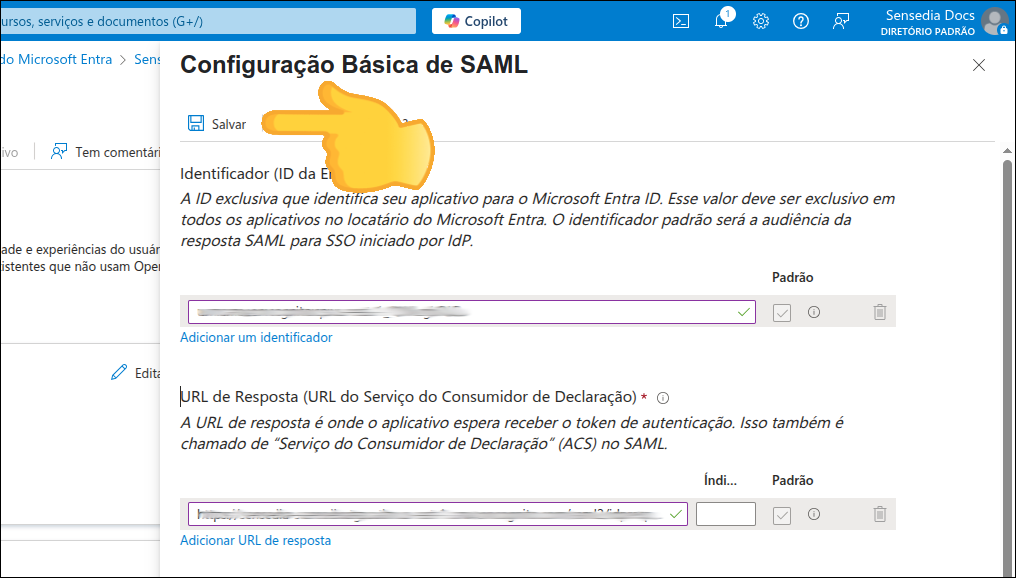
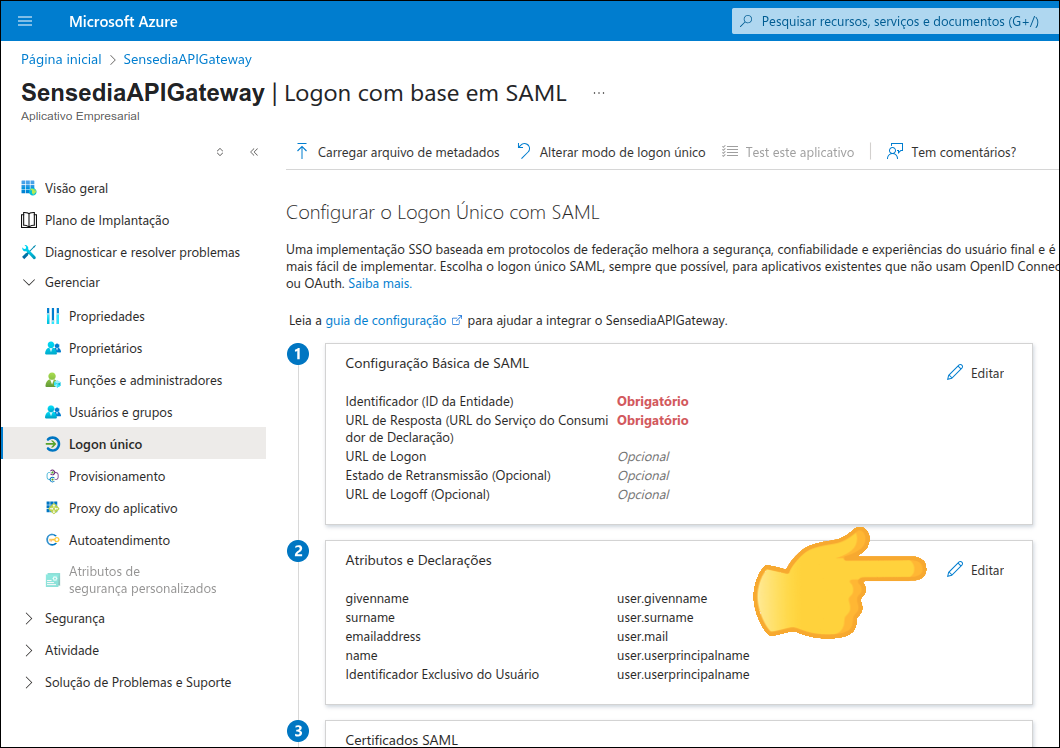
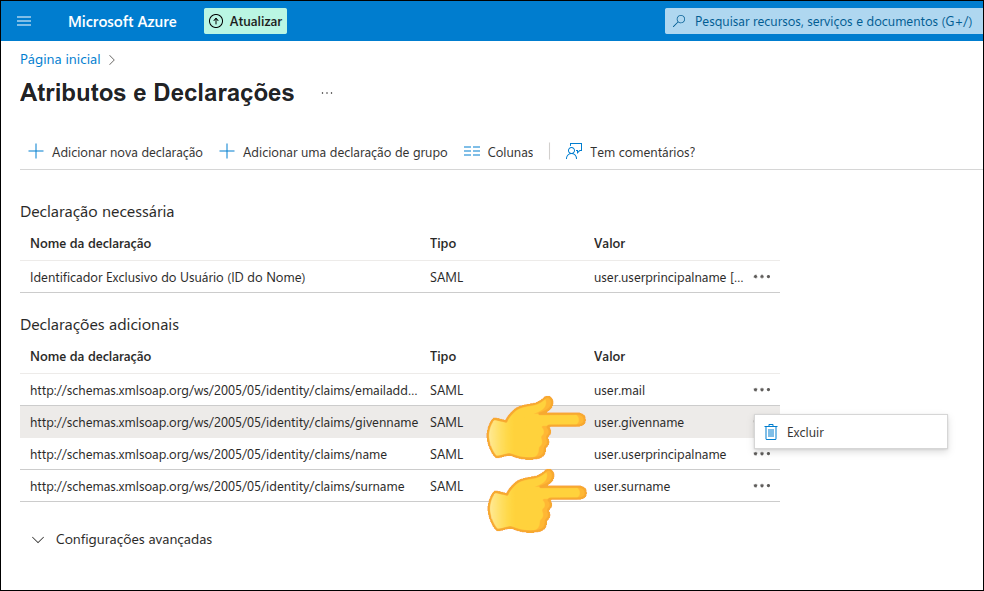
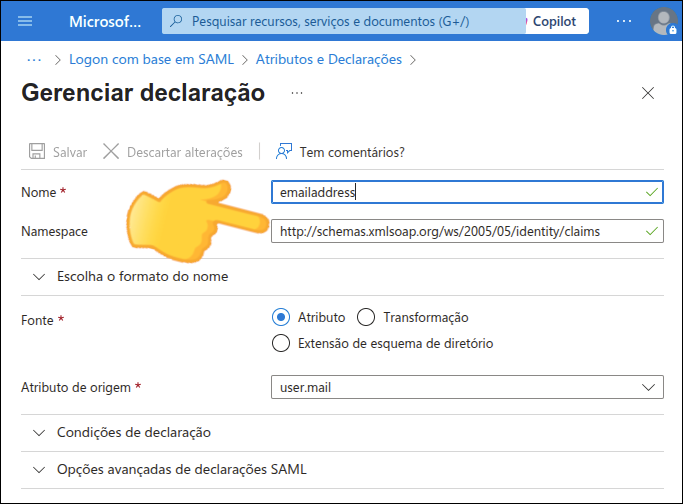
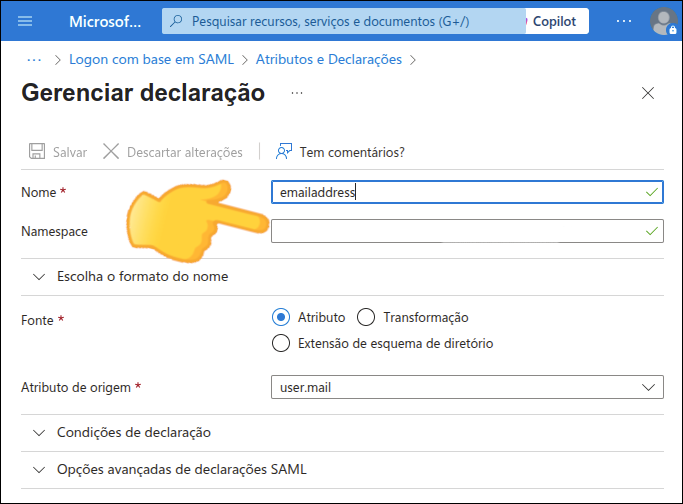
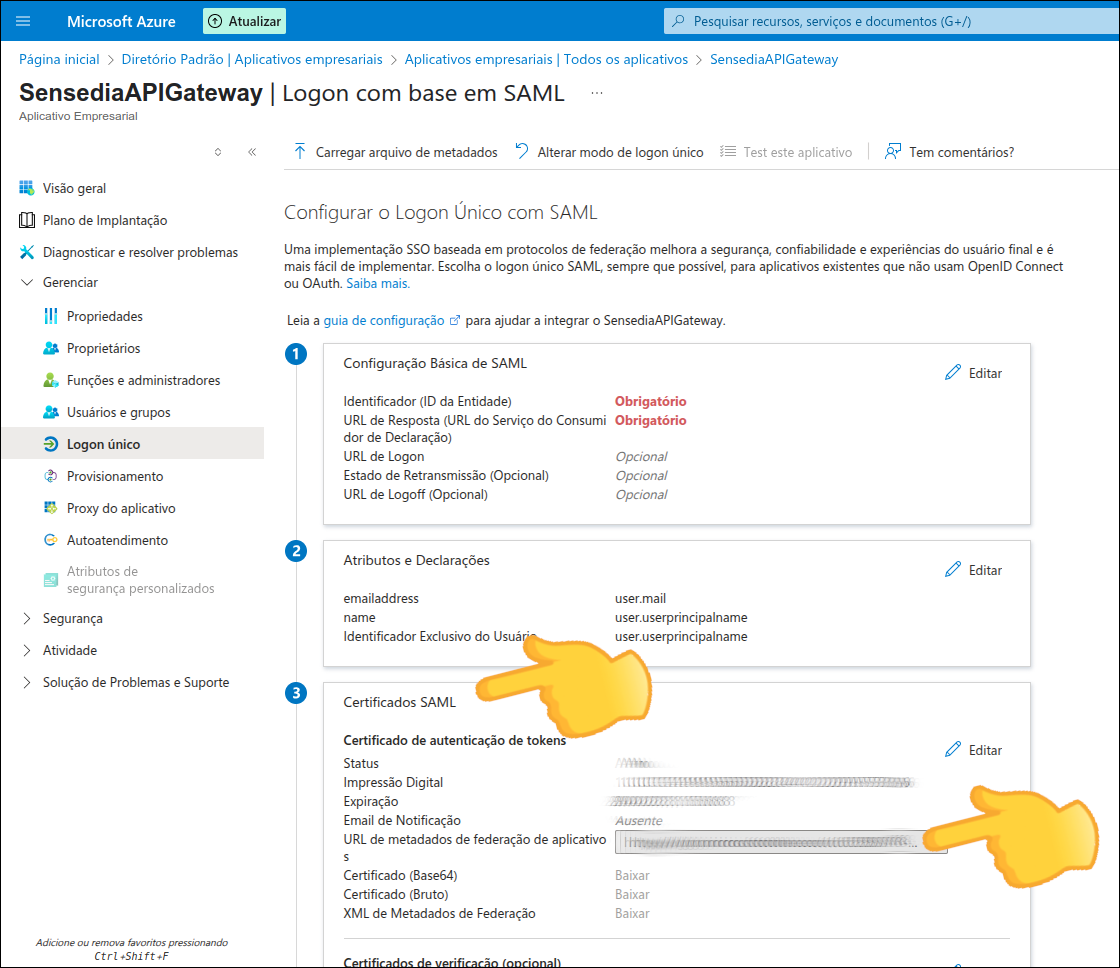
To configure Azure AD as an identity provider, follow these steps:
-
Configure SAML and
-
Note the Metadata URL to configure your Sensedia platform.
Share your suggestions with us!
Click here and then [+ Submit idea]