CSRF Generator
This interceptor is used to ensure that the origin of incoming requests is legitimate and to prevent CSRF attacks.
To prevent CSRF, the interceptor must be added to the response flow of operations other than GET (that is, it applies to operations that include or modify data).
It works like this: when a request is made to a resource containing CSRF Generator, a second token following the settings defined by the user is created. This token must then be validated by a CSRF validation interceptor.
| If the OAuth interceptor is already inserted in the flow, there’s no need to add the CSRF Generator/CSRF Validation interceptors to prevent attacks, since the OAuth feature imposes the inclusion of a token in the call. |
| These interceptors are recommended when the API is open (without OAuth or client ID authentication). |
Configuring the interceptor
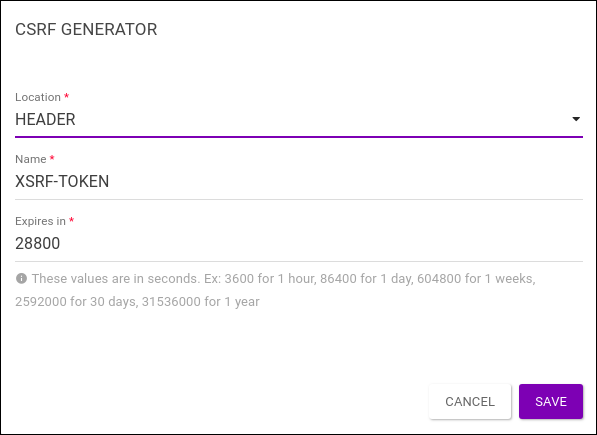
To configure the interceptor (see image below), inform the location of the token (e.g., header or cookie), a unique name, and the length of time in which the token will be valid (in seconds, in the field Expires in).
Share your suggestions with us!
Click here and then [+ Submit idea]