Connectivity models
The data plane can be connected to private environments for:
1 - Backend consumption of the public gateway pool, as shown in diagram 1:
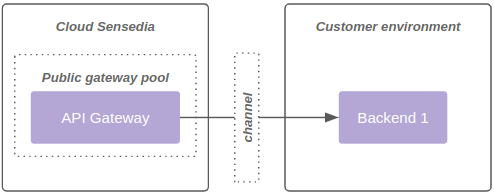
2 - Consumption of the private gateway pool, as shown in diagram 2:
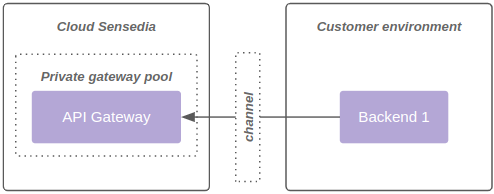
| A gateway pool cannot be public and private at the same time. |
Supported connectivity models
Allow list (Default)
-
Positive aspects
-
Most recommended model due to practicality and resilience.
-
Each data plane has at least 2 fixed output IPs. These IPs can/should be used for customer-side firewall controls.
-
To further enhance security, an mTLS strategy can be used between the gateways and the backend.
-
Cost already included in standard offers.
-
-
Limitations
-
It is not possible to access backends without externalization through a proxy or similar technology.
-
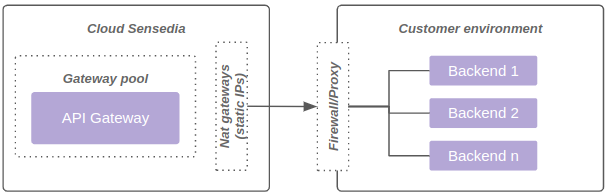
The diagram below represents connectivity through Allow list:
VPN (on request)
-
Positive aspects
-
Model with private access, ensuring secure communication between Gateways and Backends.
-
-
Attention points
-
Shared responsibility between Sensedia and the customer for configuring and maintaining connectivity.
-
SLA may differ for environments with VPN due to a higher incidence of network issues.
-
Higher setup, maintenance, and troubleshooting costs.
-
Communication occurs directly between Gateways and Backends, with no support for outbound NAT.
-
Gateways operate in an auto-scaling environment, which means that new IPs can be dynamically assigned within the configured range. Therefore, the entire range of IPs allocated to the data plane must be allowed, making it impossible to allocate only specific IPs (e.g., /32).
-
-
Limitations
-
Each data plane can connect to up to 4 networks, limited to 8190 IPs.
-
BGP (Border Gateway Protocol) is not supported in the current model.
-
There is no native support for NAT, which means that the communication between Gateways and Backends always occurs with the Gateways' original IPs.
-
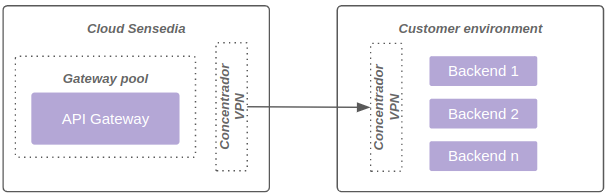
The diagram below represents connectivity through VPN:
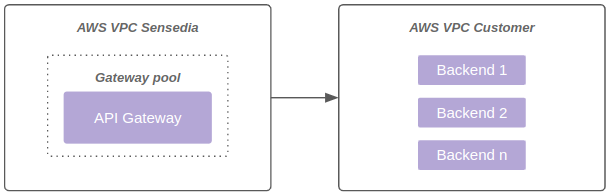
VPC Peering (on request)
-
Positive aspects
-
Stability and resilience.
-
Simplified setup.
-
-
Attention points
-
Offer available only to customers whose backend is also allocated on AWS.
-
-
Limitations
-
Each data plane can be connected to up to 4 networks, limited to 8190 IPs.
-
The diagram below represents connectivity through VPC Peering:
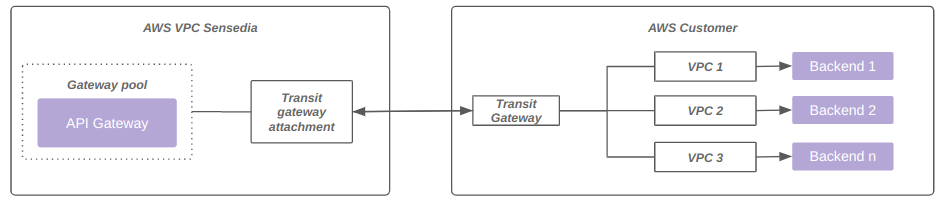
Transit Gateway (on request)
-
Positive aspects
-
Possibility to access backends through a private link.
-
No need to use VPN.
-
Greater communication flexibility between VPCs.
-
Within AWS limits, regarding Transit Gateway and connectivity, essential points are adjustable.
-
For more information, see the AWS Transit Gateway Limits documentation.
-
-
Attention points
-
Customer must share AWS Transit Gateway using their Sensedia account.
-
Need to create routes on the Sensedia side and on the client side.
-
The AWS billing fee happens on both sides (Customer and Sensedia), as AWS charges per VPC attached to the AWS Transit Gateway, and it happens on both sides.
-
-
Limitations
-
Each data plane can receive up to 5 unique AWS Transit Gateway attachments.
-
AWS Transit Gateway limits also apply.
-
The diagram below represents connectivity through Transit Gateway:
| For more information on the process of establishing connectivity using AWS Transit Gateway, visit this link. |
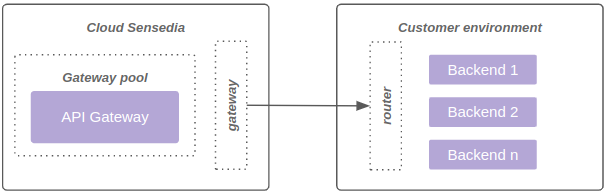
Direct Connect (on request)
-
Positive aspects
-
Possibility to access backends through a private link.
-
-
Attention points
-
Cost.
-
Shared responsibility model between Sensedia, customer and link provider.
-
-
Limitations
-
Each data plane can be connected to up to 4 networks, limited to 8190 IPs.
-
The diagram below represents connectivity through Direct Connect:
| Networks above 8190 hosts (/19) are not supported. |
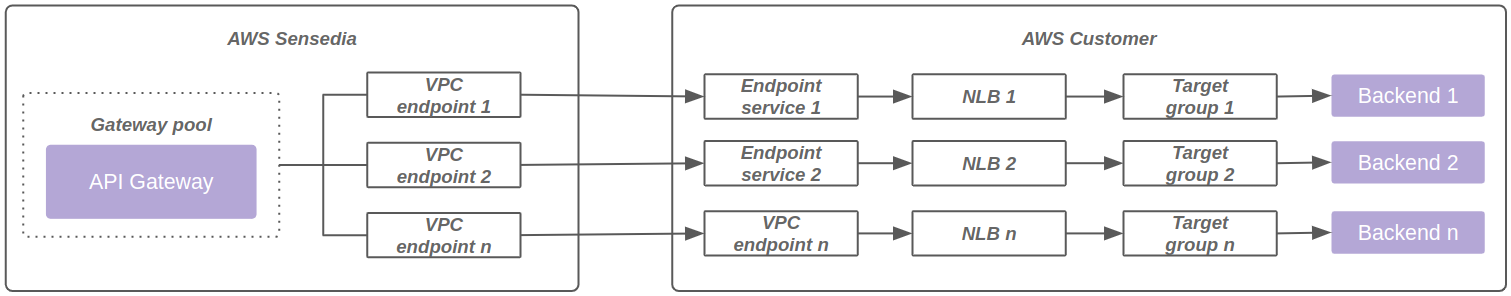
Private link (on request)
-
Positive aspects
-
Facilitates communication between components on AWS.
-
Ensures private access with high resiliency.
-
For more information, see official AWS documentation.
-
-
Negative aspects
-
Requires exposure through NLB on the customer side.
-
-
Private DNS name
-
As per the AWS documentation, it is possible to use a name with a custom domain (
<service>.customer.com.br, for example) in the endpoint service. This name is considered private because AWS registers it in a DNS zone local to the VPCs connected to the endpoint service. -
The advantage is being able to consolidate the service exposure under a unique name for different service consumers.
-
For customers wishing to use this functionality, it is necessary to enable and validate the endpoint service to use the selected name. Once configured, the customer must open a ticket with Sensedia support, requesting the activation of the private DNS name and providing the relevant endpoint service information.
-
-
Limitations
-
Up to 4 VPC endpoints (powered by AWS Private link) are supported per data plane.
-
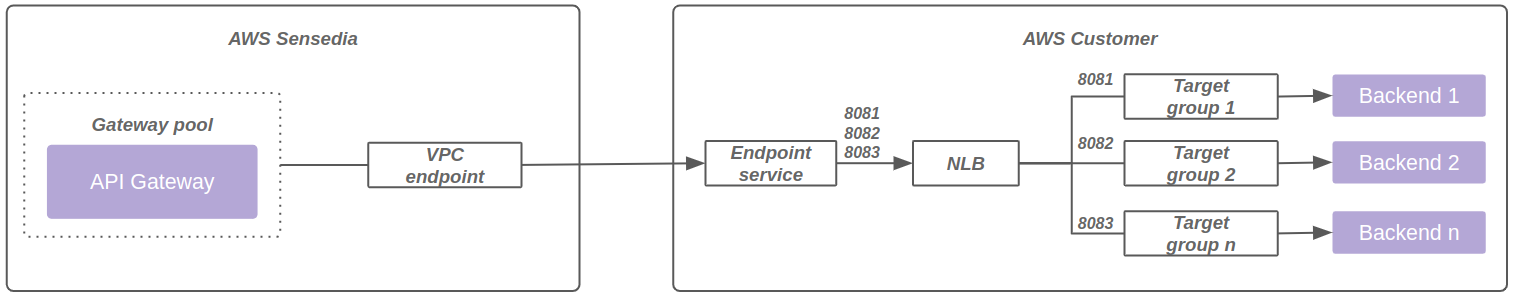
The diagram below represents connectivity using VPC endpoint powered by AWS Private link:
Additionally, it is possible to use the same VPC endpoint associated with the same load balancer, with multiple ports and target groups. The diagram below represents this model:
Share your suggestions with us!
Click here and then [+ Submit idea]