Creating, Editing and Deleting an Inbound Address
Creating a new inbound address
To register a new inbound address, click the Create Inbound Address button, represented by the + symbol on the bottom right corner of the Inbound Address screen.
The fields to be filled in vary according to your gateway type and the protocols you accept.
| If you use an Open Ecosystems product and want to create an inbound address for use in the Open Ecosystems context, there is an extra field to check and some options are fixed. Go to this page to see about the creation form in that case. |
Hybrid gateway
When the API Platform is deployed to a hybrid environment, the responsibility for communication security is the client’s. Therefore, regardless of the protocol supported, the user must only type in the inbound address and then reference it when registering the desired environment to deploy APIs. You can read more about this here.
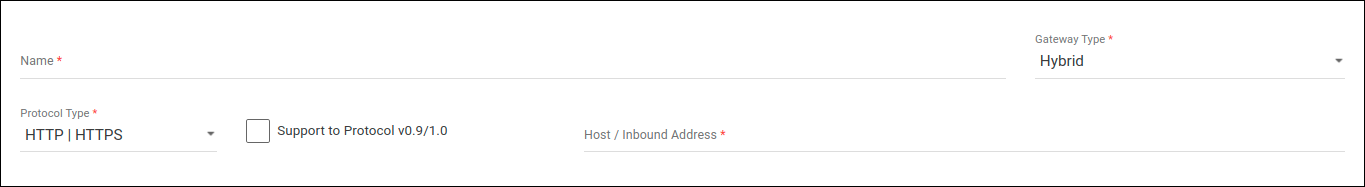
The fields to fill in are:
-
Name: name identifying the address. It can be equal to the host address itself or something more descriptive.
-
Gateway Type: in this case, select Hybrid.
-
Data Plane: select the data plane to be linked to this inbound address. This field ensures data segregation by data plane, so that ingress traffic and its certificates are routed and stored exclusively in the correct environment.
-
If the gateway type is Hybrid, it will not be possible to select a SaaS data plane.
-
-
Protocol Type: protocol(s) you accept (HTTP; HTTPS; HTTP|HTTPS).
-
If the protocol is HTTP, the option Support to Protocol v0.9/1.0 will be checked by default and can’t be unchecked. If the protocol is HTTPS or HTTP|HTTPS, the option will be unchecked by default but may be checked.
-
-
Host/Inbound Address: type here the address itself. It will be the host of environments where APIs are deployed.
| For hybrid gateways, you don’t need to use DNS. You can insert an IP address or port. |
SaaS gateway
For SaaS gateways, the fields you need to configure vary according to the types of protocol accepted.
HTTP
If the only protocol accepted is HTTP, this means that no TLS security will be applied. In this case, the user must only type in the address in DNS format and then reference it when registering the desired environment to deploy APIs. You can read more about this here.
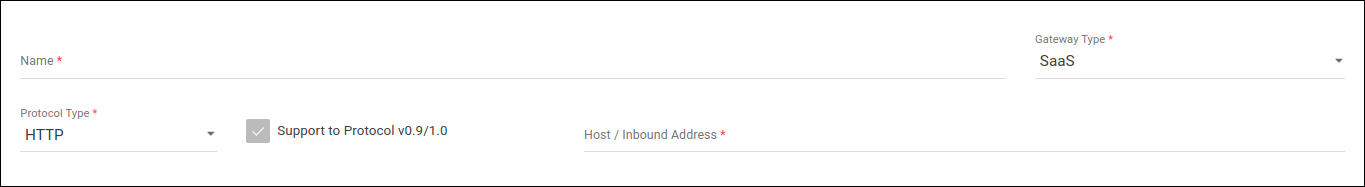
The fields to fill in are:
-
Name: name identifying the address. It can be equal to the host address itself or something more descriptive.
-
Gateway Type: in this case, select SaaS.
-
Data Plane: select the data plane to be linked to this inbound address. This field ensures data segregation by data plane, so that ingress traffic and its certificates are routed and stored exclusively in the correct environment.
-
If the gateway type is SaaS, it will not be possible to select a Federated data plane.
-
-
Protocol Type: protocol you accept (select HTTP).
-
The option Support to Protocol v0.9/1.0 will be checked by default and can’t be unchecked.
-
-
Host/Inbound Address: type here the address itself as a DNS name. It will be the host of environments where APIs are deployed.
HTTPS or HTTP|HTTPS
When you accept only HTTPS or both HTTP and HTTPS (HTTP|HTTPS), you can choose the type of security applied: TLS or mTLS.
In addition to the security options, the user must type in the host address in DNS format and then reference it when registering the desired environment to deploy APIs. You can read more about this here.
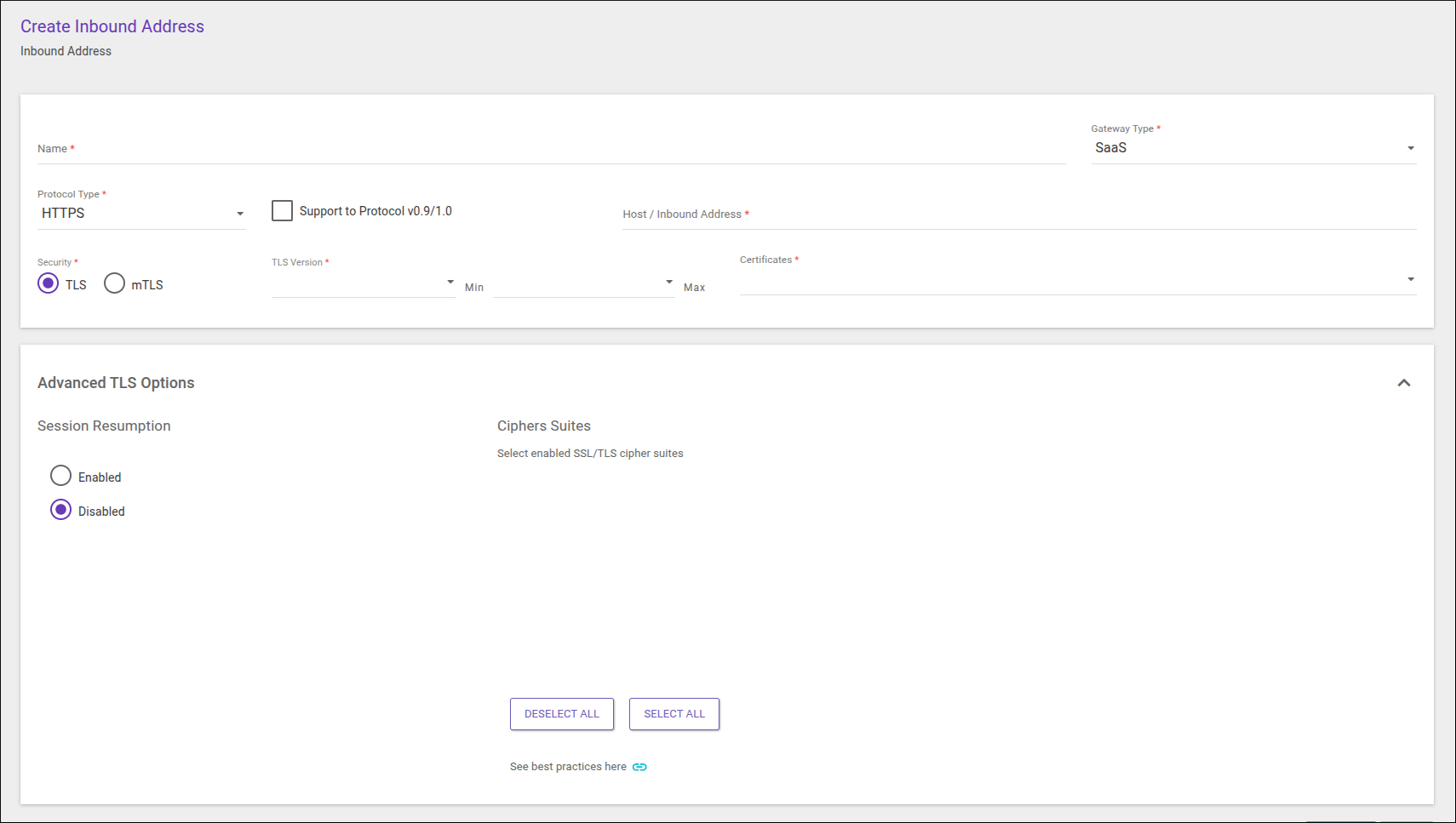
The fields to fill in are the same regarding HTTPS and HTTP|HTTPS:
-
Name: name identifying the address. It can be equal to the host address itself or something more descriptive.
-
Gateway Type: in this case, select SaaS.
-
Data Plane: select the data plane to be linked to this inbound address. This field ensures data segregation by data plane, so that ingress traffic and its certificates are routed and stored exclusively in the correct environment.
-
If the gateway type is SaaS, it will not be possible to select a Federated data plane.
-
-
Protocol Type: protocol you accept (select HTTPS or HTTP|HTTPS).
-
The option Support to Protocol v0.9/1.0 will be unchecked by default and may be checked.
-
-
Host/Inbound Address: type here the address itself as a DNS name. It will be the host of environments where APIs are deployed.
-
Security: security type (TLS or mTLS)
-
TLS Version: two fields to define the range of TLS versions supported. Options: versions 1.0, 1.1, 1.2 e 1.3.
-
The Min field must contain the lowest version supported while Max must contain the highest. Thus, if you choose
1.0and1.3, it means you support all version (from 1.0 to 1.3). If you choose1.2and1.3, you support only versions 1.2 and 1.3. To support only one version, select it on both fields (e.g.,1.3,1.3). The version on the Min field can’t be higher than that on the Max field.
-
| For the sake of simplification, we are calling all versions "TLS version", but the official terminology is SSL 1.0 and 1.1 and TLS 1.2 and 1.3. It’s worth noting that mTLS is only applicable to TLS versions 1.2 and 1.3 (versions 1.0 and 1.1 are obsolete). |
-
Certificate: field to select a certificate that is registered on the Certificates screen.
-
It must be an inbound certificate.
-
Advanced TLS options
In this section, there are specific settings for TLS Session Resumption and Cipher Suite, which give more control in the TLS security level to adjust it as needed. To edit these settings, simply click on the arrow at the right side of TLS Advanced Options.
-
TLS Session Resumption: Allows you to enable or disable TLS Session Resumption as needed. By default, it is always enabled, even if the advanced TLS settings are not edited. To enable it, click Enable and to disable it, click Disable.
| If the inbound address is in an Open Ecosystems context, by default this option will be disabled. Go to this page to read more about. |
-
Ciphers Suites: here you can choose specific ciphers that should be the only ones accepted by the inbound address, note that by default, all are accepted. The list shows the ciphers relative to the previously chosen TLS version range. You can choose all or clear the current selection via the Select All and Deselect All buttons below the list.
| It is only possible to set the cipher suite for TLS versions 1.0 to 1.2. For version 1.3 all ciphers are accepted. |
Ciphers list
TLSv1.0
1 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA #ECDHE-RSA-AES256-SHA
2 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA #ECDHE-RSA-AES128-SHA
3 TLS_RSA_WITH_AES_256_CBC_SHA #AES256-SHA
4 TLS_RSA_WITH_AES_128_CBC_SHA #AES128-SHA
TLSv1.1
1 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA #ECDHE-RSA-AES256-SHA
2 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA #ECDHE-RSA-AES128-SHA
3 TLS_RSA_WITH_AES_256_CBC_SHA #AES256-SHA
4 TLS_RSA_WITH_AES_128_CBC_SHA #AES128-SHA
TLSv1.2
1 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA #ECDHE-RSA-AES256-SHA
2 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA #ECDHE-RSA-AES128-SHA
3 TLS_RSA_WITH_AES_256_CBC_SHA #AES256-SHA
4 TLS_RSA_WITH_AES_128_CBC_SHA #AES128-SHA
5 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 #ECDHE-RSA-AES256-GCM-SHA384
6 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 #ECDHE-RSA-AES128-GCM-SHA256
7 TLS_RSA_WITH_AES_256_GCM_SHA384 #AES256-GCM-SHA384
8 TLS_RSA_WITH_AES_128_GCM_SHA256 #AES128-GCM-SHA256
TLSv1.3
9 TLS_AES_256_GCM_SHA384 #TLS_AES_256_GCM_SHA384
10 TLS_CHACHA20_POLY1305_SHA256 #TLS_CHACHA20_POLY1305_SHA256
11 TLS_AES_128_GCM_SHA256 #TLS_AES_128_GCM_SHA256
Cifra não suportada do TLS 1.2
TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305 #ECDHE-RSA-CHACHA20-POLY1305Editing an inbound address
You can edit an inbound address listed on the Inbound Address screen.
Click the ![]() icon on the Actions column and you’ll be redirected to the editing screen, which is like the registration screen.
icon on the Actions column and you’ll be redirected to the editing screen, which is like the registration screen.
| Any modification will be reflected on all environments that have the given inbound address as the host. |
Deleting an inbound address
To delete an inbound address, click the ![]() icon on the Actions column of the list of existing addresses and click Confirm.
icon on the Actions column of the list of existing addresses and click Confirm.
| An inbound address can’t be deleted if it’s being used as the host of an environment. |
Share your suggestions with us!
Click here and then [+ Submit idea]