Connectivity Models
The data plane can be connected to public and private environments for:
-
Consumption of the public backend for the integration, as shown in diagram 1:
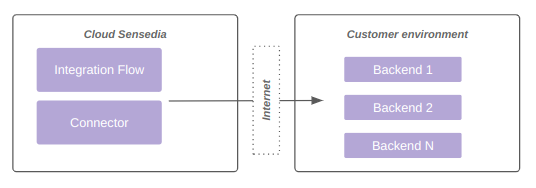
-
Consumption of the private backend, as shown in diagram 2:
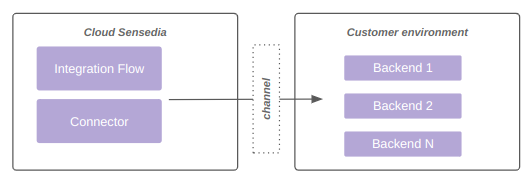
Supported connectivity models
Allow list (default)
-
Pros
-
Most recommended model for practicality and resilience.
-
Each data plane has at least 2 fixed outbound IPs. These IPs can/should be used for client-side firewall controls.
-
Cost is included in standard offerings.
-
-
Limitations
-
Cannot access backends without externalization through a proxy or similar technology.
-
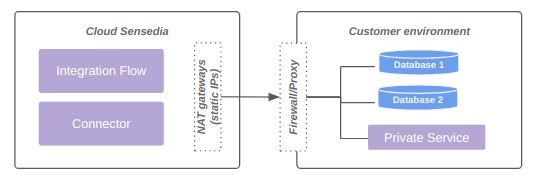
The diagram below represents connectivity via allow list:
VPN (upon request)
-
Pros
-
Provides private access.
-
-
Considerations
-
Shared responsibility.
-
Different SLA for environments with VPN due to high incidence of issues.
-
Higher cost for setup, maintenance, and troubleshooting.
-
-
Limitations
-
Each data plane can connect to up to 4 networks, limited to 8190 IPs.
-
BGP is currently not supported.
-
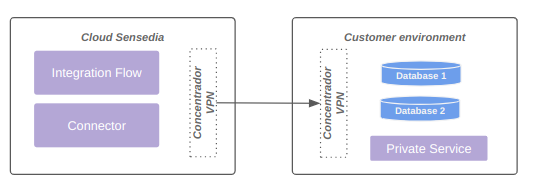
The diagram below represents connectivity via VPN:
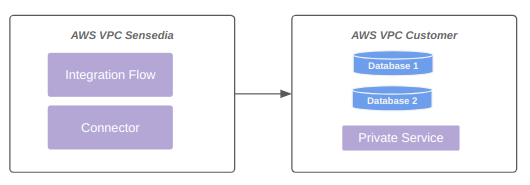
VPC peering (upon request)
-
Pros
-
Stability and resilience.
-
Simplified setup.
-
-
Considerations
-
Available only for clients whose backend is also hosted on AWS.
-
-
Limitations
-
Each data plane can connect to up to 4 networks, limited to 8190 IPs.
-
The diagram below represents connectivity via VPC peering:
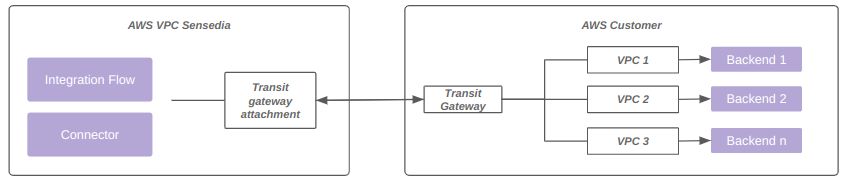
Transit gateway (upon request)
-
Pros
-
Allows access to backends through a private link.
-
No need for a VPN.
-
Greater flexibility in communication between VPCs.
-
Within AWS limits, essential points related to the transit gateway and connectivity are adjustable.
-
| For more information, consult the documentation on quotas for your transit gateway. |
-
Considerations
-
The client must share the AWS transit gateway with the Sensedia account.
-
Route creation is required on both Sensedia’s and the client’s sides.
-
AWS charges apply on both sides (Client and Sensedia) for VPCs attached to the AWS transit gateway.
-
-
Limitations
-
Each data plane can receive up to 5 unique AWS transit gateway attachments.
-
AWS transit gateway limits also apply.
-
The diagram below represents connectivity via transit gateway:
| For more information, access the documentation about the establishment of connectivity with AWS transit gateway. |
Direct connect (upon request)
-
Pros
-
Allows access to backends through a private link.
-
-
Considerations
-
Cost.
-
Shared responsibility model between Sensedia, the client, and the link provider.
-
-
Limitations
-
Each data plane can connect to up to 4 networks, limited to 8190 IPs.
-
The diagram below represents connectivity via direct connect:
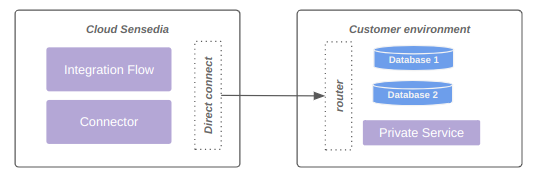
| Networks exceeding 8190 hosts (/19) are not supported. |
PrivateLink (upon request)
-
Pros
-
Facilitates communication between components on AWS.
-
Ensures private access with high resilience.
-
-
Cons
-
Requires exposure through an NLB on the client side.
-
-
Private DNS name
-
According to AWS documentation, it is possible to use a custom domain name for the endpoint service, such as <service>.customer.com.br. This name is private as AWS registers it in a local DNS zone for the VPCs connected to the endpoint service.
-
The advantage is consolidating service exposure under a single name for different service consumers.
-
Clients wishing to use this feature need to enable and validate the endpoint service to use the selected name. Once configured, the client should open a ticket with Sensedia support to activate the private DNS name, providing the endpoint service details.
-
-
Limitations
-
Up to 4 VPC endpoints (powered by AWS PrivateLink) are supported per data plane.
-
The diagram below represents connectivity using a VPC endpoint enabled by AWS PrivateLink:
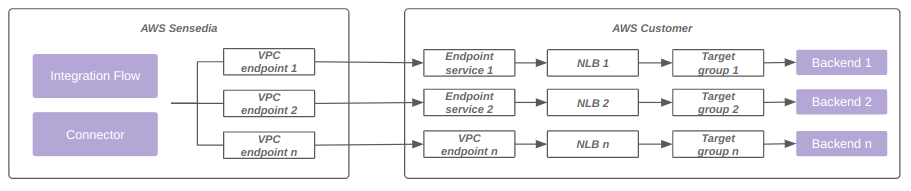
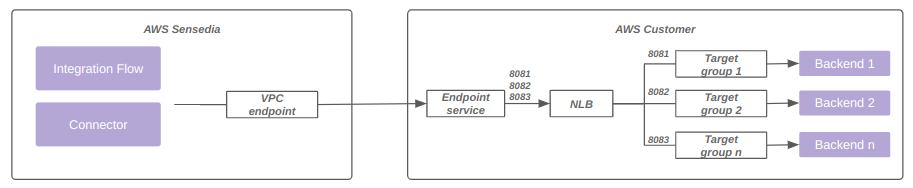
Additionally, the same VPC endpoint associated with a single load balancer can be used with multiple ports and target groups.
The diagram below represents this model:
| For more information, consult the official AWS documentation on PrivateLink. |
Share your suggestions with us!
Click here and then [+ Submit idea]